Fraudsters' Favorite Disposable Emails
During my investigations around disposable/temporary emails, I came across a subset of email domains heavily used by fraudsters and cybercriminals:
While a lot of disposable emails are used by people who want a throwaway email to avoid spam, or who may be tempted to create multiple accounts, these email domains are heavily used for account takeover (stealing user accounts) and spam.
I have bad news for you. If you are reading this article because you saw one of the email domains above on your accounts, e.g. if it has been set as a recovery email, then it probably means your account has been hacked and accessed by someone else.
How do cybercriminals use these disposable emails?
By searching for these email domains across the web, we encounter 3 main use cases:
- Fake account creation
- Spam
- Account takeover
Fake account creation
Email domains, such as tenermail.com, related to https://firstmail.ltd, make it easy to create and instrument thousands of email domains programmatically. Thus, it’s no surprise it’s used by fraudsters to create a lot of fake accounts on different online services.
In the screenshot below, from a popular cybercriminal forum, we see that the user created a script to manage 1,000 accounts on Steam created using tenermail.com emails.
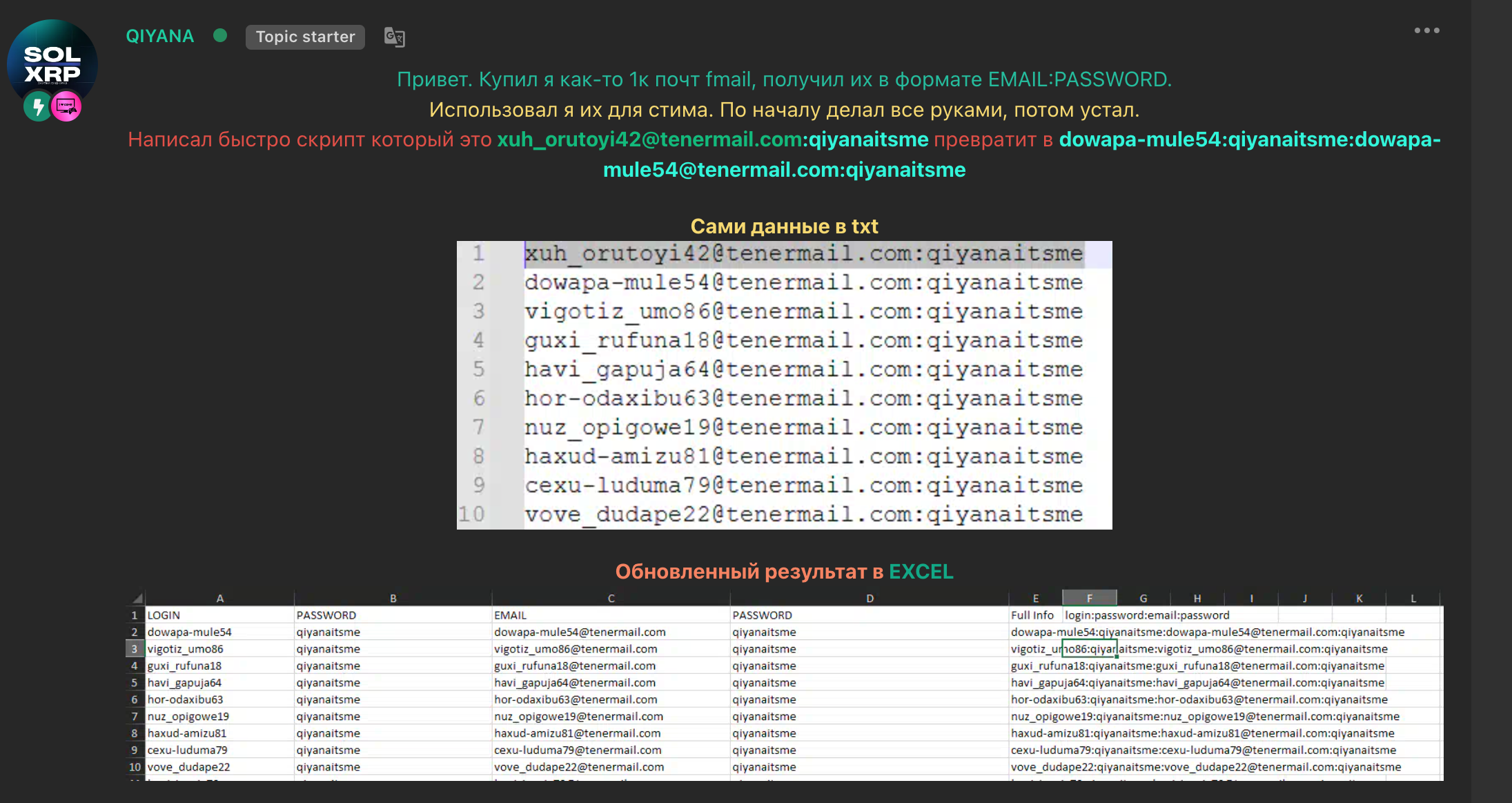
Once translated, we can read the following:
Hi. I once bought 1k fmails, received them in the EMAIL:PASSWORD format.I used them for steam. At first I did everything manually, then I got tired.
I quickly wrote a script that will turn this
xuh_orutoyi42@tenermail.com :qiyanaitsme into dowapa-mule54:qiyanaitsme:dowapa-mule54@tenermail.com:qiyanaitsme
Spam
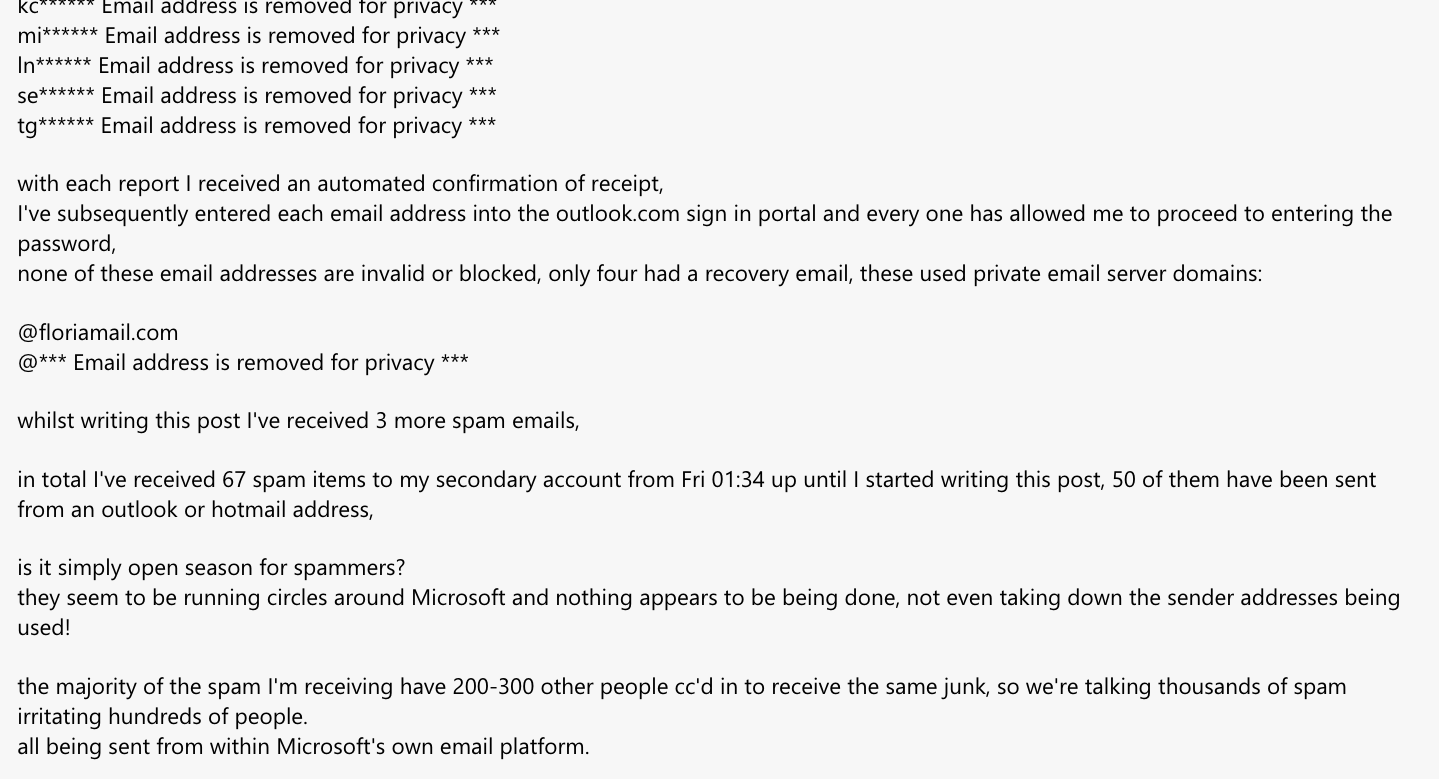
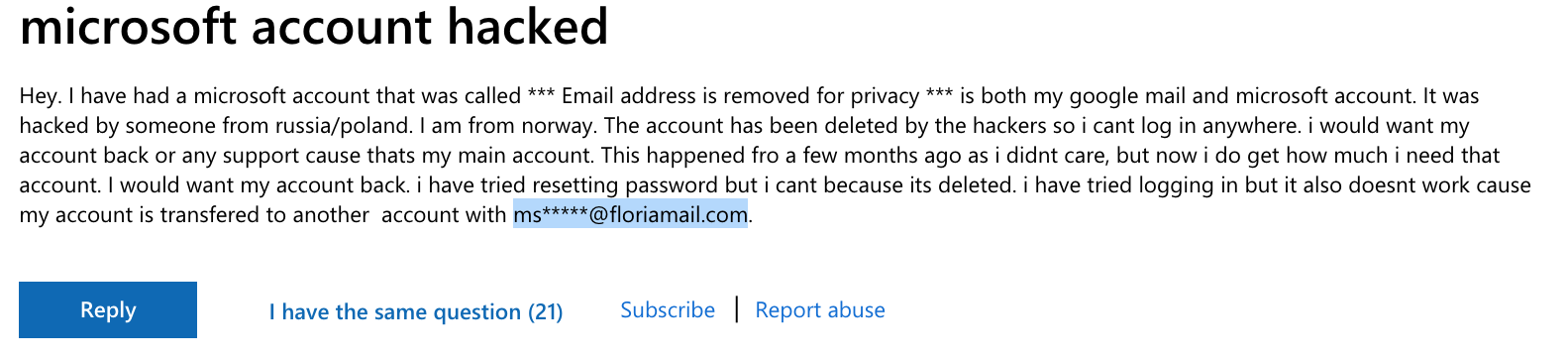
Another popular use case for these disposable emails is spam. In the screenshot below, coming from the Microsoft forum, we see a user complaining about receiving spam from emails linked to the floriamail.com email domain that is not properly stopped by Microsoft.
Account takeover
Finally, the most popular use of these disposable emails by cyber criminals is to steal user accounts, i.e. to conduct account takeover attacks. Indeed, once cyber criminals get access to a victim account, e.g. by using bots that conduct credential stuffing attacks, they change the recovery email to an email they control that belongs to jugarmail.com, tenermail.com, floriamail.com, senoramail.com, lapasamail.com and sfirstmail.com. Thus, it enables attackers to take full control of the victim account.
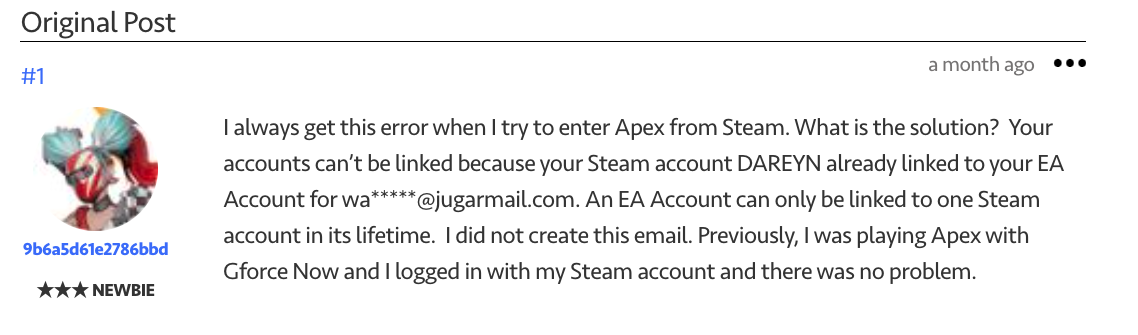
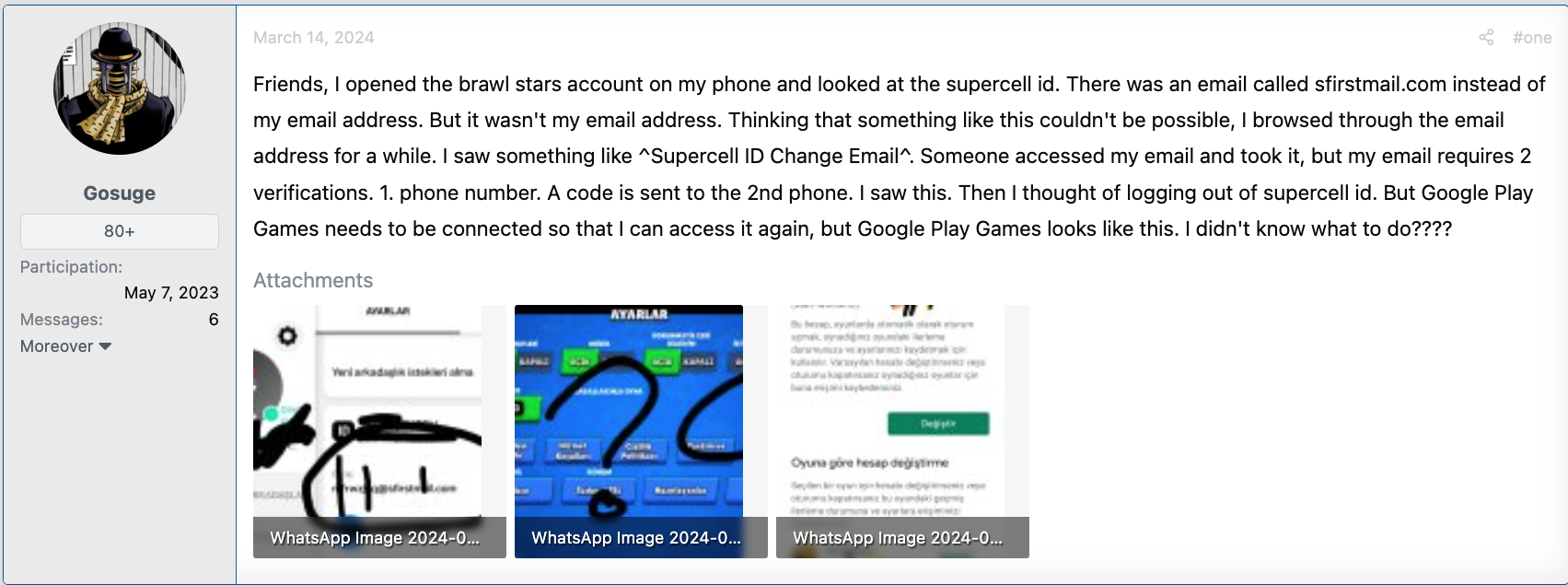
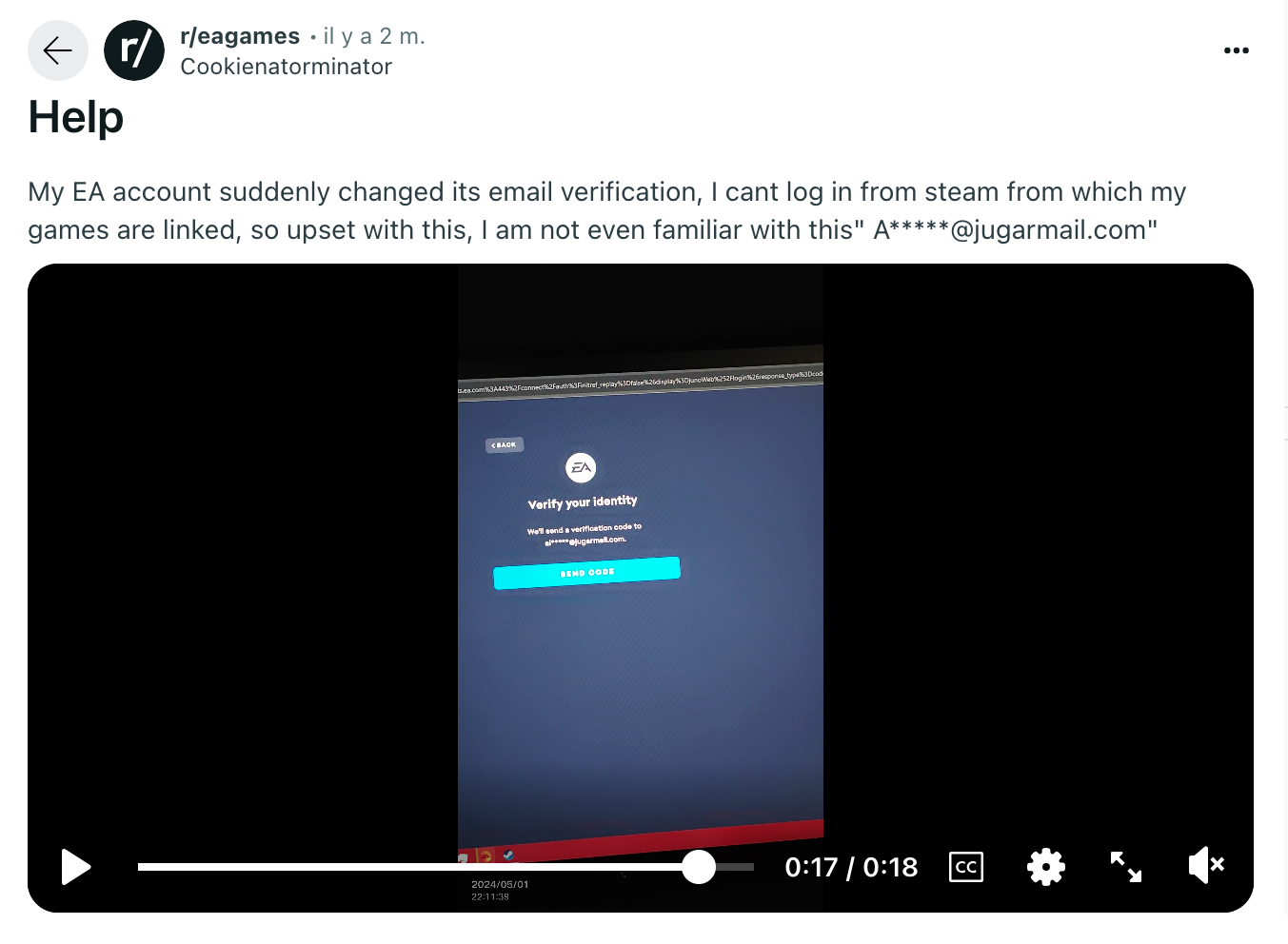
In the following screenshots, we see several victims whose Microsoft, Steam, Electronic Arts (EA) and Supercell accounts have been breached. Every time, the attackers modified the recovery email to point to disposable emails that can’t be tied to their identity.
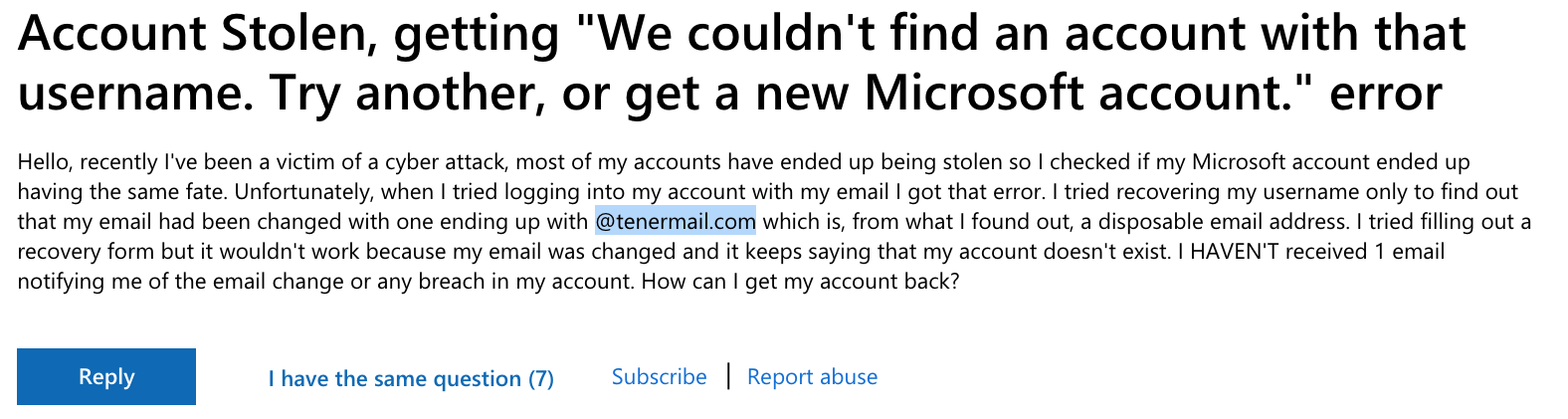
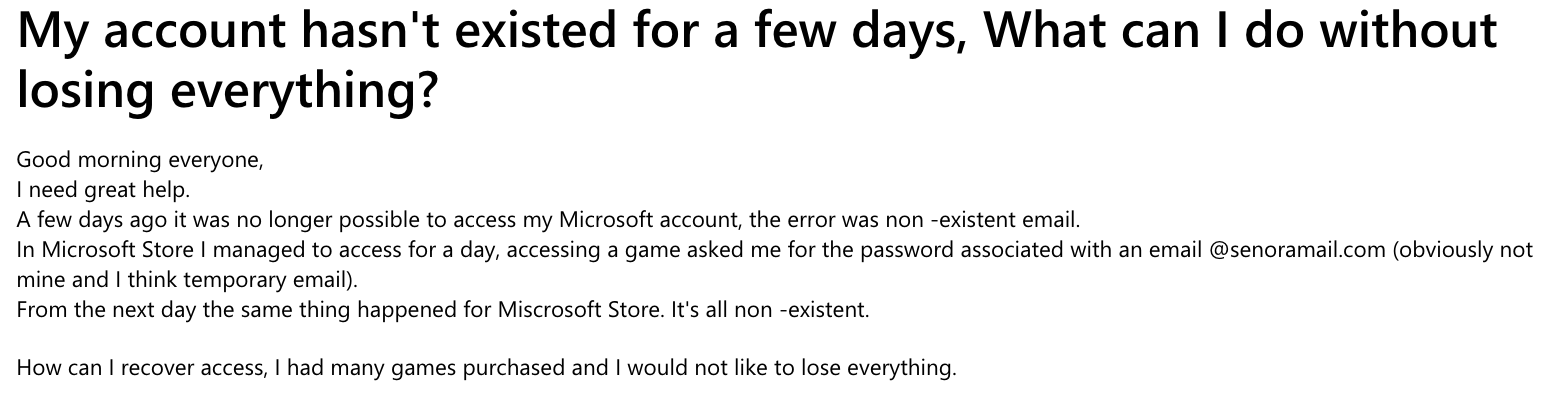
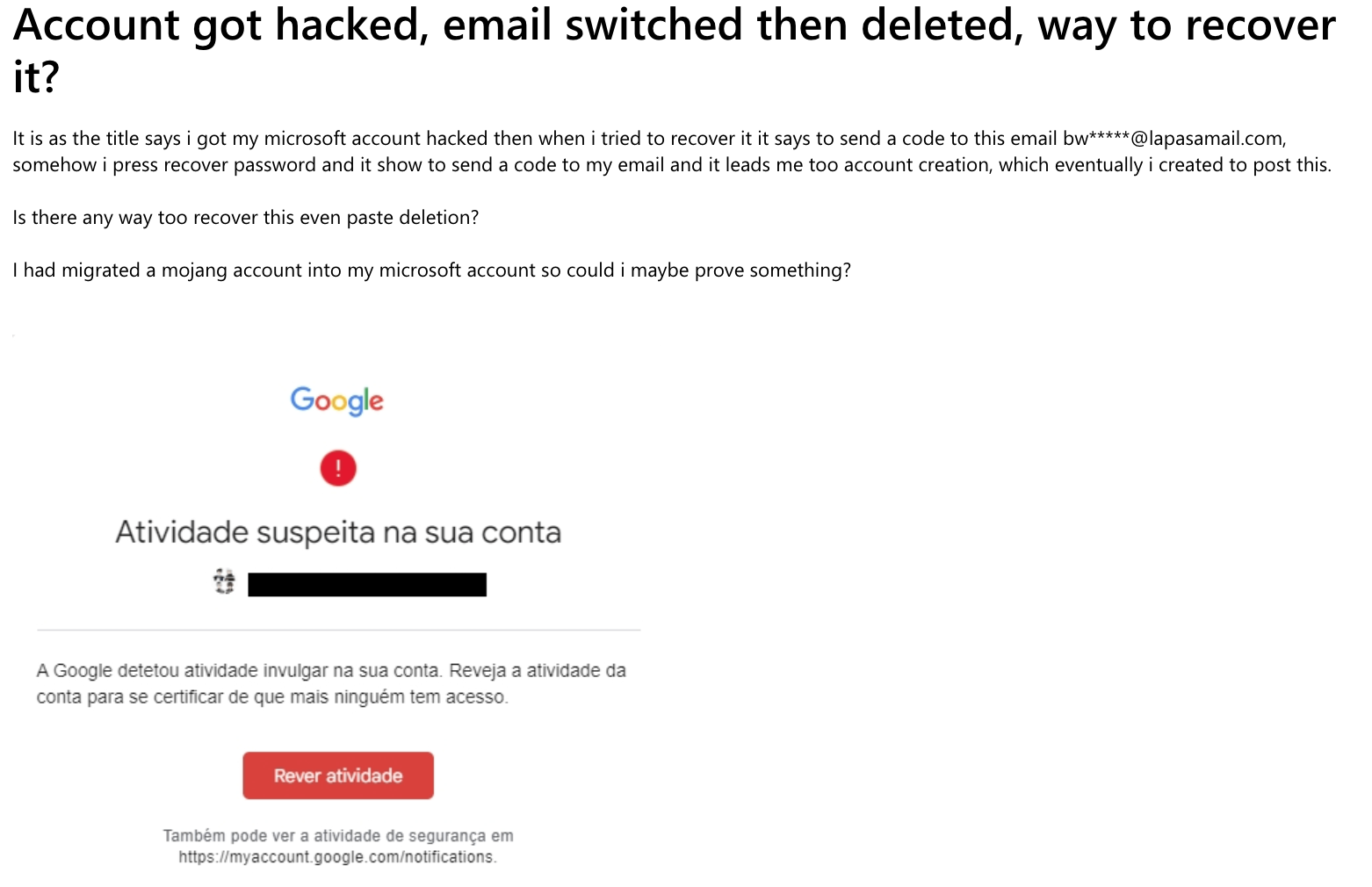
Besides Microsoft accounts, cybercriminals particularly like to target video game platforms:
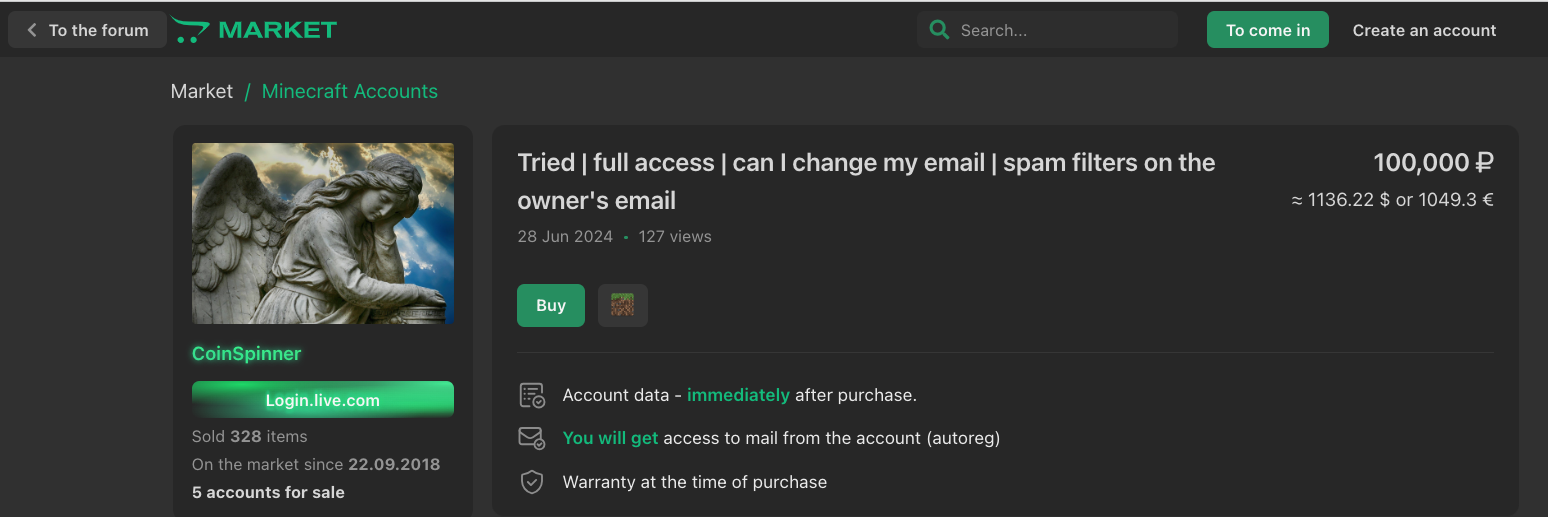
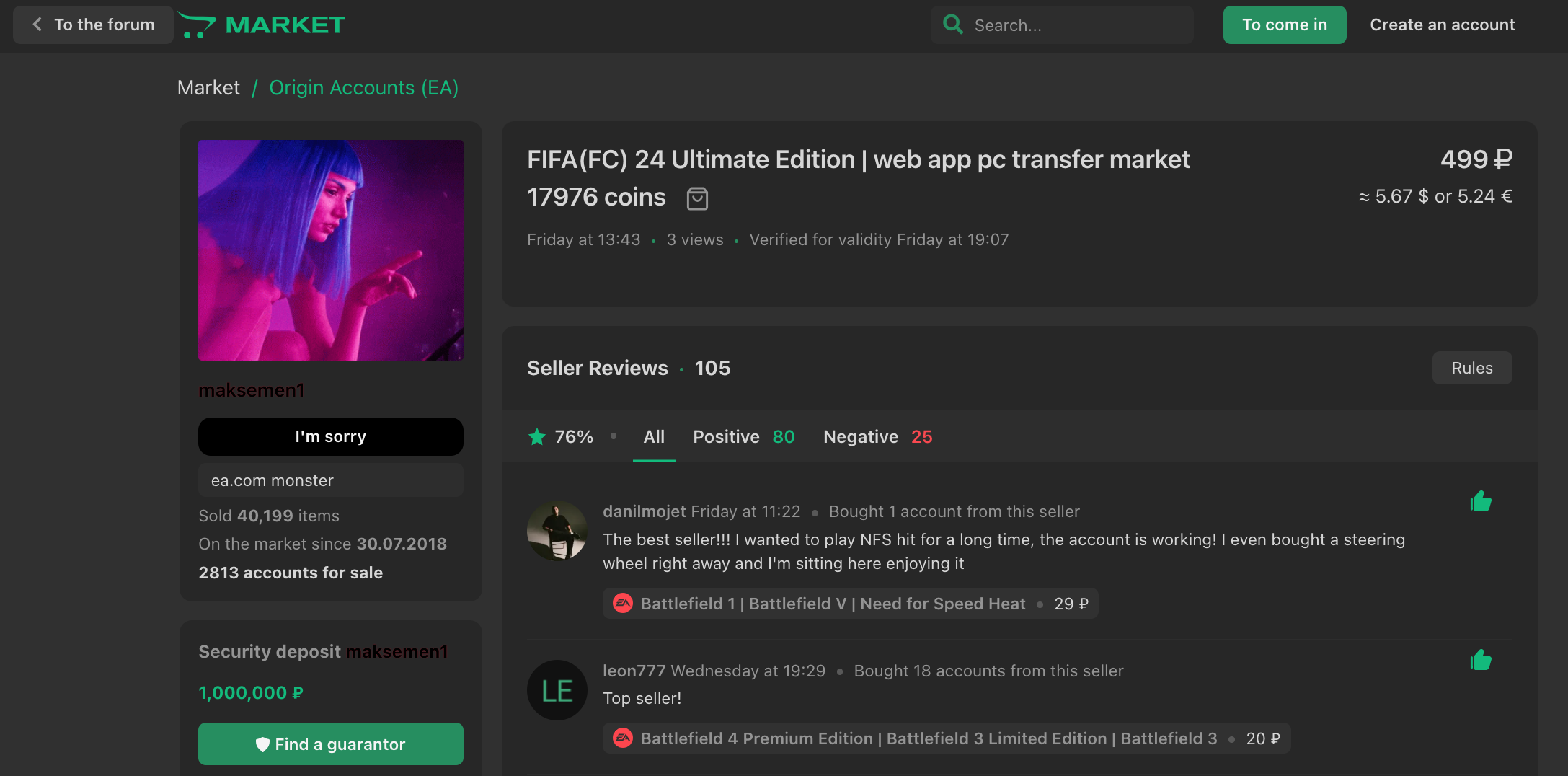
On the other side of the spectrum, we encounter cybercriminals selling access to these stolen accounts by using the disposable emails they set as recovery emails (screenshots are translated from Russian using Google Translate)
What can you do about it?
For end users
If you are a “normal”/end-user who found one of the following email domains set as a recovery email on your account, it means your account has been hacked (except if you set it yourself of course): jugarmail.com, tenermail.com, floriamail.com, senoramail.com, lapasamail.com, sfirstmail.com, menormail.com, and nietamail.com.
In this case, contact the support of the website and:
- Change your password: use a password manager to generate a secure and unique password. In case you used the same password across different websites, I recommend you change your password everywhere.
- Use multi-factor authentication to add another layer of security to your accounts.
In general, if your account got breached it may mean that:
- Your password got stolen using a malware running on your device or because you got provided it on a phishing page.
- You used the same password/a known password across different services and an attacker conducted a successful credential stuffing attack.
For companies operating websites and mobile applications
Bot protection: You should put in place protections against credential stuffing attacks, such as a bot protection tool like DataDome.
MFA: You should also incentivize your users to activate and use multi-factor authentication. Even though it’s no silver bullet, it will make the life of attackers more difficult.
Monitoring after login: Account takeover doesn’t stop once the account is accessed after login. You should monitor critical actions, such as recovery email modification to detect abnormal patterns. For example, you can use this list of disposable email domains (also accessible through an API) to detect users who want to change the recovery email to a disposable one. The same thing applies to temporary phone numbers.