Benchmarking proxy IP lists: FireHOL vs Device and browser info (May 2025)
In this post, we benchmark FireHOL’s
firehol_proxies list against
the device and browser info proxy detection database. Our goal is to understand where public blocklists fall
short, especially when it comes to detecting residential and ISP proxy infrastructure commonly used by
fraudsters and sophisticated bots to distribute their attacks. While FireHOL remains a valuable open source
resource, our results show that defenders relying solely on public feeds are likely to miss large segments
of fast-moving or evasive proxy traffic.
Before we dive in: this is not a critique of FireHOL. It’s a long-running, community-maintained project that makes IP lists freely available, a service that helps defenders of all sizes.
Our aim is to understand where public intel (like FireHOL’s proxy list) diverges from proprietary detection. In particular, we’re interested in better understanding the constitution of open datasets, their geographical distribution, and whether or not they focus mostly on certain types of proxies (residential vs data center)
Indeed, proxy IP addresses are a foundational signal in fraud detection and bot detection. For fraud analysts and security teams, it’s critical to understand what public lists miss. Depending on how a proxy dataset is built—and which providers or collection methods it relies on, you’ll surface very different parts of the threat landscape.
For example, scrapers and sneaker bots may favor one type of proxy network, while financial fraud or account takeover tools lean on mobile and residential IPs. If a dataset doesn’t cover those sources, it may give a false sense of coverage.
Overview of the 2 proxy lists/databases
What is FireHOL?
FireHOL is a community-driven project that aggregates multiple IP lists to help defenders block known malicious or unwanted traffic. While originally built as a firewall management tool, it’s now best known for its curated threat intel feeds, including lists of open proxies, Tor exit nodes, and known spam sources.
The proxy list we benchmark against is
firehol_proxies, a feed
updated daily that combines several open proxy datasets e.g. ip2proxy_px1lite,
socks_proxy_30d, sslproxies_30d .
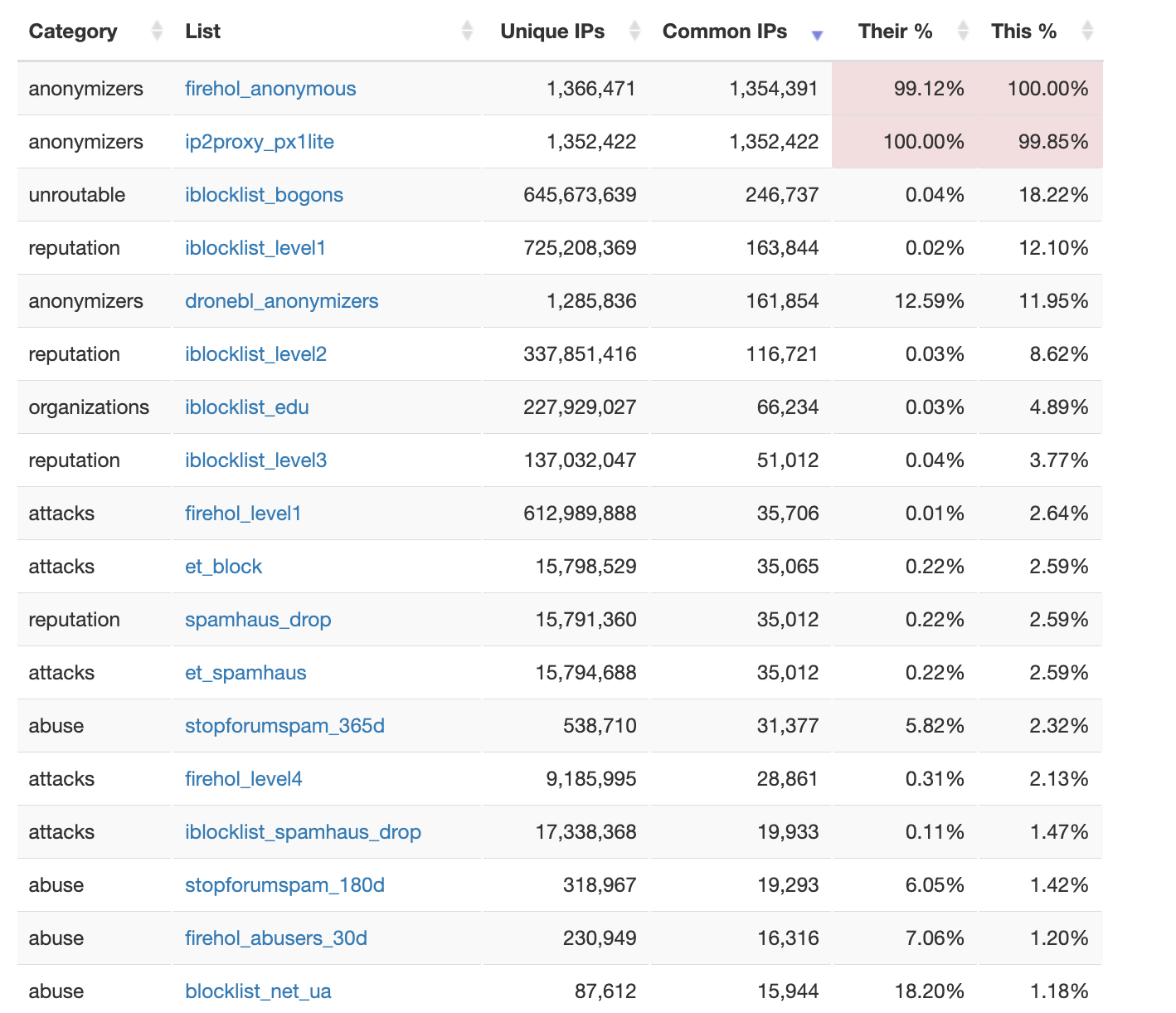
The screenshot below shows the main sub-lists constituting
the firehol-proxies list.
What is the device and browser info proxy database?
This is a proprietary, curated proxy IP database built from real-world proxy infrastructure. Unlike FireHOL, it does not include any public or third-party threat feeds. The dataset includes:
- Residential, ISP and data center proxies
- Free and paid proxy services
- Tor exit nodes
- Proxy sources commonly used in scraping, scalping, credential stuffing, fake account creation, and payment fraud
Every proxy IP included has been verified as actively used as a proxy. The list is updated continuously, with a fresh build published every six hours.
Comparison of device and browser info proxy database vs Firehol proxies
To understand the strengths and limitations of each list, we compared basic dataset characteristics: size, ASN diversity, geographic distribution, and proxy type coverage.
| Metric | Device & Browser Info DB | FireHOL firehol_proxies |
| Unique proxy IPs | 5,516,253 | 1,349,380 |
| Unique ASNs | 25,301 | 14,065 |
| Unique countries | 235 | 207 |
| Source model | Fully proprietary and curated | Aggregated from public lists |
| Includes residential/ISP proxies? | Yes (extensive coverage) | Very limited |
Our dataset is over 4× larger and includes more IPs from more ASNs and countries. This reflects deeper visibility into real-world proxy infrastructure, especially evasive types like residential, ISP, and mobile proxies that rarely show up in public threat feeds.
🌍 Geographic distribution
The table below focuses on the geographic distribution of the proxy IPs of both databases (top 10). Both datasets contain proxy IPs from a wide range of countries: 235 for device and browser info vs 207 for Firehol. The top country for Firehol is the US, with 363k proxy IPs, while for device and browser info it is the Brazil, with 620K proxy IPs. However, device and browser info DB still contains more than 558K US proxy IPs. It also contains a wide range of proxies from diverse countries such as Russia, the UK and India.
| Rank | Device & Browser Info DB | FireHOL |
| 1 | BR (Brazil): 620,612 | US (United States): 363,340 |
| 2 | VN (Vietnam): 583,968 | RU (Russia): 106,341 |
| 3 | US (United States): 558,827 | CN (China): 98,233 |
| 4 | RU (Russia): 285,974 | UA (Ukraine): 56,063 |
| 5 | MA (Morocco): 174,929 | DE (Germany): 53,229 |
| 6 | MY (Malaysia): 171,281 | GB (United Kingdom): 47,948 |
| 7 | TR (Turkey): 169,744 | SG (Singapore): 40,988 |
| 8 | ZA (South Africa): 139,865 | IN (India): 38,231 |
| 9 | GB (United Kingdom): 117,723 | FR (France): 35,679 |
| 10 | IN (India): 108,697 | ZA (South Africa): 29,452 |
🇺🇸 Top US ASNs: better visibility into residential and ISP infrastructure
US-based services are common targets for automated abuse, especially credential stuffing, fake account creation, scraping and scalping. To blend in, attackers often rely on proxies that originate from legitimate consumer networks like Comcast, AT&T, or Verizon.
We analyzed the top 30 US ASNs by proxy IP count in each dataset. While both lists include major cloud providers, the device and browser info dataset surfaces far more IPs from residential networks., while these networks tend to be underrepresented in FireHOL’s proxy list.
Key findings:
- Device and browser info includes 55% more US-based proxy IPs than FireHOL (558K vs 363K).
- Both lists are topped by Amazon ASNs (likely due to widespread use of cloud
instances), but beyond that, the coverage diverges:
- Comcast (44K), AT&T (43K), T-Mobile (20K), and Verizon (UUNET, 14K) appear prominently in our dataset.
- These ISPs are either missing or well below the top 30 in FireHOL, which focuses more on data centers.
- FireHOL lists many hosting-focused ASNs: DigitalOcean, Google Cloud, Microsoft Azure, etc., networks commonly used by open proxies but less effective for residential-scale fraud.
- This difference matters: most public blocklists often focus on data center IPs, but tend to be blind to the IPs fraudsters are actually using in production, residential IPs.
| AS Organization (Device and browser Info proxy DB) | IP Count |
|---|---|
| AMAZON-AES | 50,459 |
| AMAZON-02 | 45,448 |
| COMCAST-7922 | 44,075 |
| ATT-INTERNET4 | 42,651 |
| AS-VULTR | 20,225 |
| T-MOBILE-AS21928 | 20,072 |
| BUNNY-COMMUNICATIONS-GLOBAL | 19,413 |
| COGENT-174 | 15,483 |
| UUNET | 14,425 |
| CHARTER-20115 | 9,772 |
| ASN-CXA-ALL-CCI-22773-RDC | 9,558 |
| CELLCO-PART | 9,079 |
| ANL-36 | 8,606 |
| AS-COLOCROSSING | 7,128 |
| TWC-10796-MIDWEST | 6,301 |
| EGIHOSTING | 6,174 |
| GTT Communications Inc. | 5,964 |
| CABLE-NET-1 | 5,917 |
| TWC-20001-PACWEST | 5,855 |
| ORACLE-BMC-31898 | 5,742 |
| Mercury Telecom LLC | 5,650 |
| TWC-11426-CAROLINAS | 5,538 |
| ADCIL-ASN-01 | 5,342 |
| WINDSTREAM | 5,316 |
| TIER-NET | 5,292 |
| BHN-33363 | 5,220 |
| HYPEENT-SJ | 5,205 |
| HostRoyale Technologies Pvt Ltd | 5,006 |
| Datacamp Limited | 4,839 |
| FRONTIER-FRTR | 4,781 |
| AS Organization (Firehol proxy list) | IP Count |
|---|---|
| AMAZON-02 | 58,845 |
| AMAZON-AES | 27,072 |
| AS-COLOCROSSING | 18,628 |
| DIGITALOCEAN-ASN | 15,473 |
| COGENT-174 | 14,793 |
| VISAFONE | 10,300 |
| ATT-INTERNET4 | 7,870 |
| SERVER-MANIA | 7,408 |
| GOOGLE-CLOUD-PLATFORM | 7,319 |
| MICROSOFT-CORP-MSN-AS-BLOCK | 7,071 |
| AS-VULTR | 6,659 |
| 3xK Tech GmbH | 5,976 |
| AS-SPRIO | 5,671 |
| EGIHOSTING | 5,509 |
| DREAMHOST-AS | 5,231 |
| 24SHELLS | 4,666 |
| PUREVOLTAGE-INC | 4,631 |
| Oy Crea Nova Hosting Solution Ltd | 4,375 |
| QUICKPACKET | 4,262 |
| KVCNET-2009 | 3,691 |
| WINDSTREAM | 3,654 |
| HVC-AS | 3,545 |
| LARUS Limited | 3,459 |
| AS-COLOAM | 3,365 |
| Amazon Data Services Ireland Ltd | 3,150 |
| Hetzner Online GmbH | 3,131 |
| NEXEON | 3,074 |
| Alibaba US Technology Co., Ltd. | 2,572 |
| TIER-NET | 2,186 |
| Tencent Building, Kejizhongyi Avenue | 2,146 |
Minimal overlap confirms divergent coverage
We found 105,553 proxy IPs present in both datasets, primarily data center proxies that appear across multiple feeds.
- That represents 7.82% of the FireHOL list
- And only 1.91% of the device and browser info DB
This low overlap confirms that the two datasets capture very different slices of the proxy ecosystem. FireHOL reflects open, often static infrastructure aggregated from public sources. Our dataset surfaces IPs actively used in fraud, including ISP and residential ranges that rotate too quickly or quietly to show up in public lists.
Recommendations
Even though public blocklists offer a valuable starting point, relying on them alone leaves significant gaps in visibility. Based on this benchmark, we recommend:
- Don’t rely solely on public IP lists.
Open datasets like FireHOL are helpful for baseline coverage, but they tend to miss fast-moving infrastructure such as residential and ISP proxies, which are commonly used in modern fraud.
- Maintain your own proxy telemetry, if possible.
If your platform is targeted by bots, it’s worth building internal detection signals to catch evolving infrastructure early.
- Recognize that different threat actors use different proxy
sources.
Scrapers, credential stuffers, and payment fraud bots operate with different budgets and goals. Their proxy footprints vary—and your detection strategy should account for that.
- Supplement with behavioral detection.
While knowing that an IP address was recently used as a proxy, it is important to acknowledge that it is not a silver bullet for detection. This is an important signal that can be used to prevent fraud, or to investigate an attack afterward, but it should be used along with other anti-fraud and bot detection signals, such as browser fingerprinting, TLS fingerprint, and behavioral analysis.
FireHOL’s mission—freely sharing threat intelligence to help everyone improve their defenses—is important work. We support that goal, and we also maintain a free public IP blocklist that anyone can integrate into their detection pipeline.
In addition, with a free account, you can access a curated list of 1M daily unique proxy IPs, updated every 6 hours, to support your research and detection efforts.
Get access: Try our proxy detection dataset
If you want to explore the differences firsthand, you can start with our free proxy IP list.
With a free account, you’ll get access to a curated set of 50,000 proxy IPs, updated every 6 hours. It’s a good starting point to compare with your own traffic or test against other blocklists.
For teams that need a deeper evaluation, we also offer free trial access to the full 30-day proxy dataset, which includes over 5 million verified proxy IPs. The data is available in both CSV and mmdb formats to support integration and analysis workflows.
You can create a free account here, or contact us to request access to the full dataset.