A study of applications targeted by temporary phone numbers
Second (and last) blog post of our series about temporary phone
numbers. In the first blog post, we created a NodeJS-based scraper to
collect 5,340 temporary phone numbers and 393,310 messages sent to these numbers.
In this blog post, we analyze the content of the messages to better understand:
- Which websites and applications are targeted by temporary phone numbers;
- In which context these temporary phone numbers are used.
TL;DR:
- Temporary phone numbers are mostly used to create a lot of (fake) accounts on online platforms. These accounts are used to conduct malicious activity such as, phishing, spreading malware or online dating scams.
- They target all kinds of applications, but in particular:
- Social networks: TikTok, Facebook and Instagram;
- Messaging/chat applications: Discord, Telegram and WhatsApp;
- Payment applications: Paypal;
- Search engine/email providers: Google, Microsoft and Apple;
- Transportation applications: Uber and Bolt.
- AI applications such as ChatGPT and Claude are heavily targeted by temporary phone numbers as it enable users to create dozens of accounts to avoid paying for the premium version of the products, e.g. ChatGPT premium.
- A simple way for applications to detect temporary numbers (and disposable emails) is to use an API that indicates whether or not a phone number is temporary or not.
Analysing 393K messages received by temporary phone numbers
For each message, we collected the content of the message as
well as the sender. Sometimes, the sender has a proper name, e.g. Viber, but sometimes it’s just a
number. The snippet below showcases a sample of messages:
[
{ sender: '+3058', message: 'HI 459102382s8' },
{ sender: 'Finstro', message: 'OTP Code 261829' },
{ sender: 'Finstro', message: 'OTP Code 580290' },
{
sender: 'Viber',
message: 'Your Viber code: 628800 Getting this message by mistake? reports.viber.com/liEBhfio 6EQbNfKgO8O'
},
{
sender: 'Blizzard',
message: 'Your verification code is 622255. If this comes as a surprise please check your security settings in case of an account compromise. \\- Battle.net'
}
]
A first analysis shows that the messages were sent by 19,928
phone numbers/companies. The table below shows the top 15 companies that sent messages to temporary phone
numbers:
| Rank | Application | Number of messages |
| 1 | AUTHMSG | 17,392 |
| 2 | 16,295 | |
| 3 | PayPal | 14,775 |
| 4 | TikTok | 10,807 |
| 5 | Tinder | 10,019 |
| 6 | Discord | 8,561 |
| 7 | 8,473 | |
| 8 | Apple | 7,774 |
| 9 | Microsoft | 7,501 |
| 10 | Uber | 7,437 |
| 11 | 6,646 | |
| 12 | Amazon | 6,512 |
| 13 | Telegram | 6,212 |
| 14 | 5,035 | |
| 15 | Imo | 4,423 |
The name of the top sender is AUTHMSG. These are
messages related to TOTP/authentication codes. A manual analysis of these messages shows that they are linked to
2FA/TOTP when logging in, or when retrieving a forgotten password. This includes a lot of messages of the
following form:
You are retrieving your password. 460588 is your verification code, DO NOT tell anyone or your account might be stolen.These messages are linked to thousands of different companies/websites.
Categories of applications targeted by temporary phone numbers
Among the top applications that sent messages to temporary phone numbers, we observe:
- Major search engines and email providers, such as Google, Microsoft and Apple
- Social networks: TikTok, Facebook and Instagram
- Messaging/chat applications: Discord, Telegram and WhatsApp
- Transportation application: Uber
- Dating application: Tinder
- Payment application: Paypal
- Marketplace: Amazon
To better understand the types of applications targeted by temporary phone numbers, I asked ChatGPT to infer the categories of the companies that sent messages using the following prompt:
Generate a JS map or objects that maps the following application names into one of the following categories. If you're unsure, classify the application as "other":
List of the categories: Social networks, payment, email, developer tools, SMS, messaging, AI, dating, transportation, marketplace, search engine, other, streaming, betting/casino
It generated the following JS object that maps the top companies to a category.
const applicationCategories = {
// Social Networks
'TikTok': 'Social networks',
'Facebook': 'Social networks',
'Instagram': 'Social networks',
...
// Payment
'PayPal': 'payment',
'Klarna': 'payment',
...
// Streaming
'YouTube': 'streaming',
'BigoLive': 'streaming',
'Twitch': 'streaming',
'Netflix': 'streaming',
...
}
Thus, we can count the number of messages received per category, cf the bar chart below. Note that for this graph, we got rid of
AUTHMSG as this is linked to thousands of applications for which we can’t infer any category
easily.
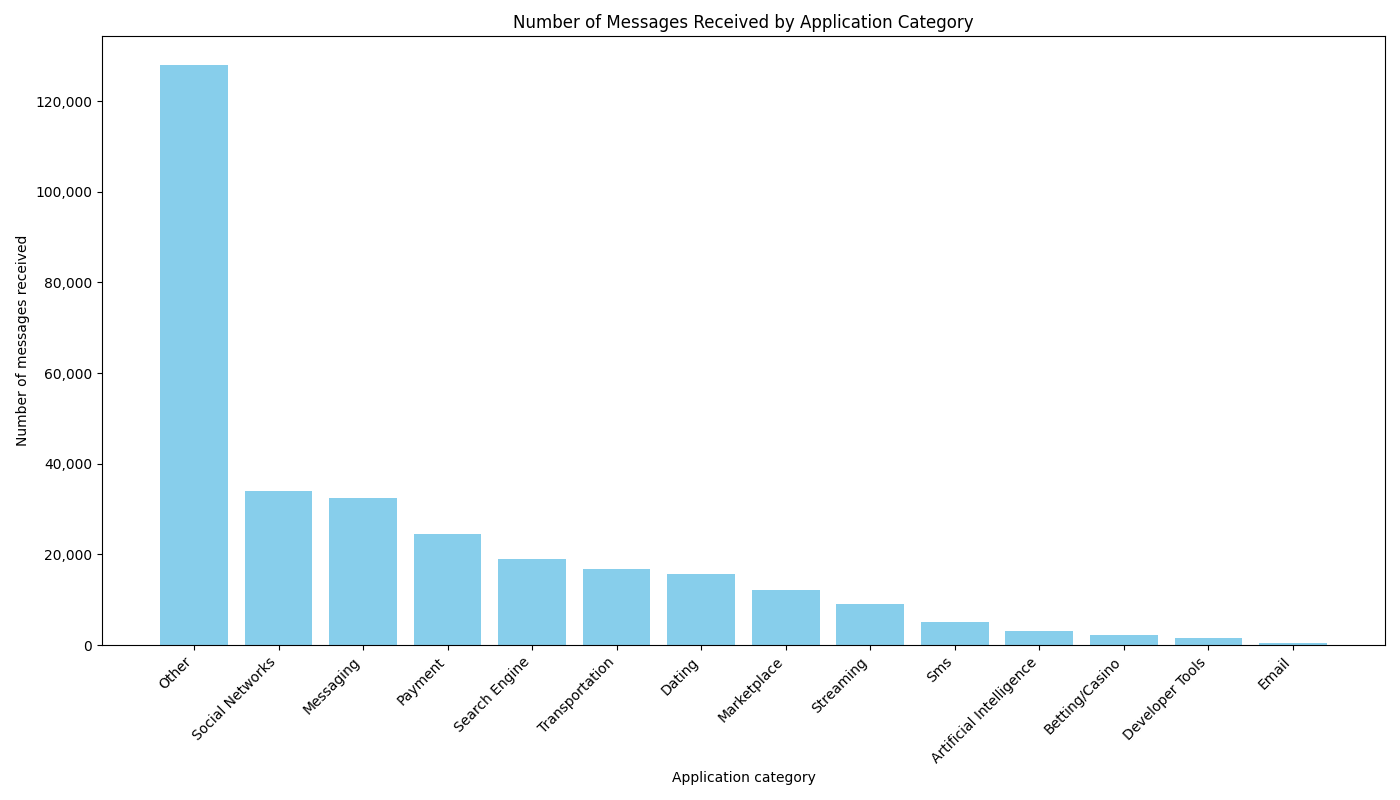
As already observed in our top 15, the most targeted categories of applications are:
- Social networks;
- Messaging/chat applications;
- Payment applications;
- Search engine/email providers;
- Transportation applications.
At the 10th position, we see that Artificial intelligence application applications are also targeted, in particular services such as ChatGPT and Claude.
Analysis of the temporary phone number messages content
To analyze the content of the message, we start by cleaning/standardizing the content of the messages:
- we delete all numbers;
- we convert all messages to lowercase;
- we delete all nonascii / whitespace characters;
We count the word frequency across all messages and obtain the following results. For better readability, we kept only words ≥ 3 characters (to get rid of all words like and, to, etc)
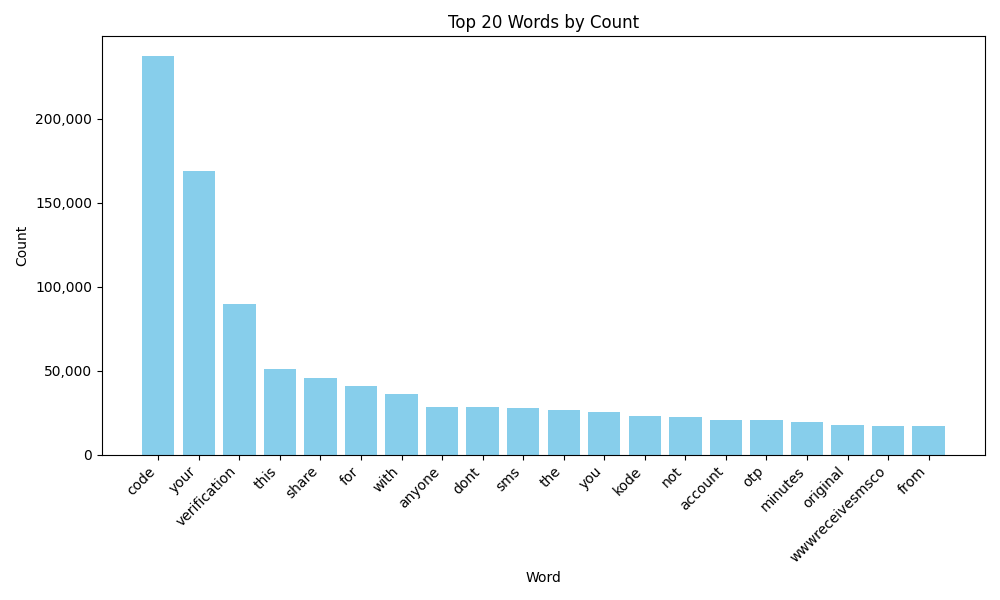
The most recurring words across all the messages sent by temporary phone numbers include:
- Code / Kode
- Verification
- OTP
Thus, this simple analysis seems to reveal that most of the SMS received by temporary phone numbers are SMS that aim to either:
- Verify the ownership of the phone number
- Ask for a 2FA/TOTP code in the context of a login/forgotten password/account creation process
Manual analysis of the messages
To confirm the previous findings, we went through thousands of messages manually. The screenshot below shows a sample of messages sent by OpenAI. We can see that these are all verification codes that are sent when creating an openAI account.
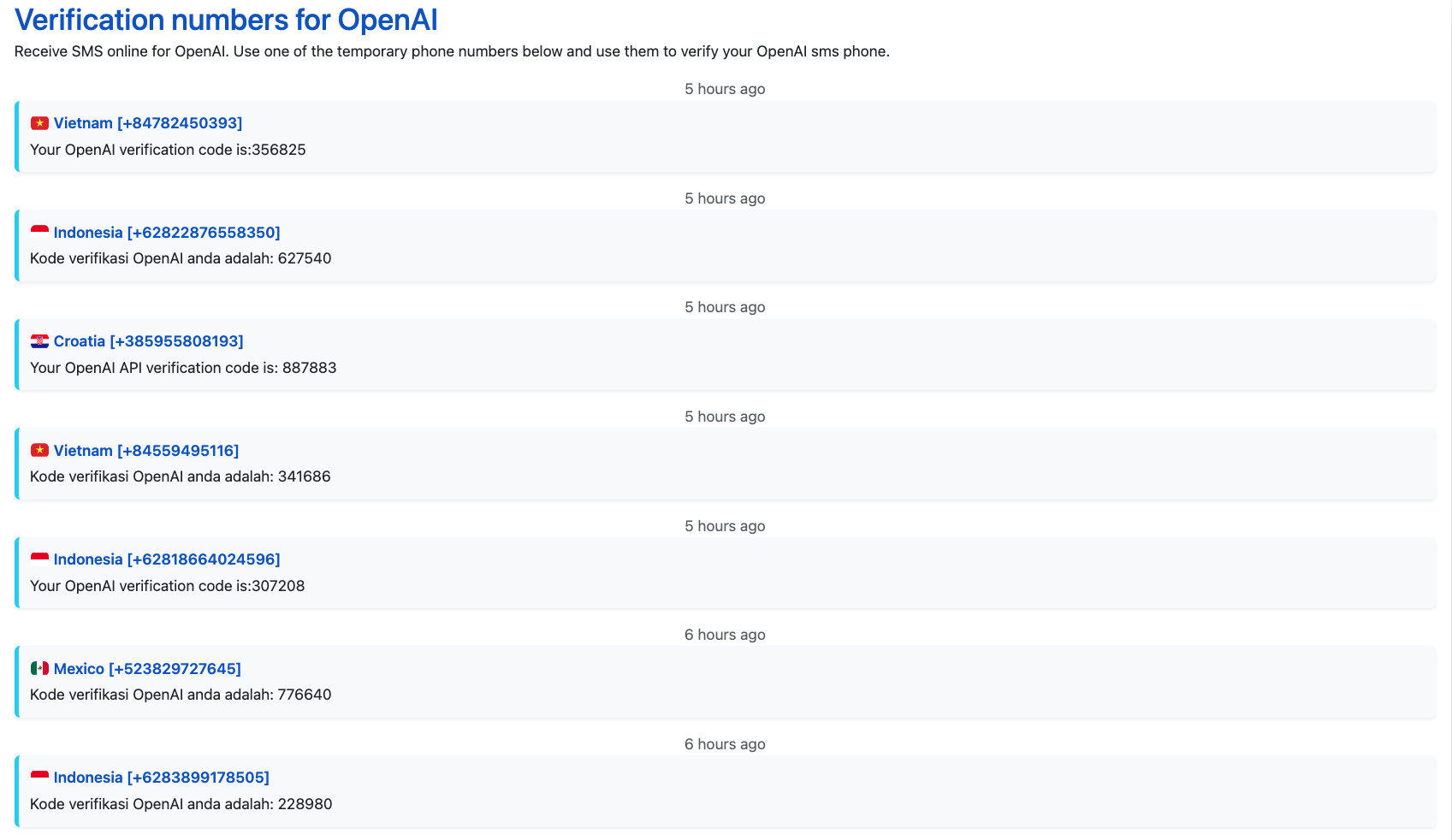
If we look at the text written on SMS24, this isn’t a coincidence. It looks like the whole SEO strategy of this website is to target people looking for temporary phone numbers that can be used to create accounts:

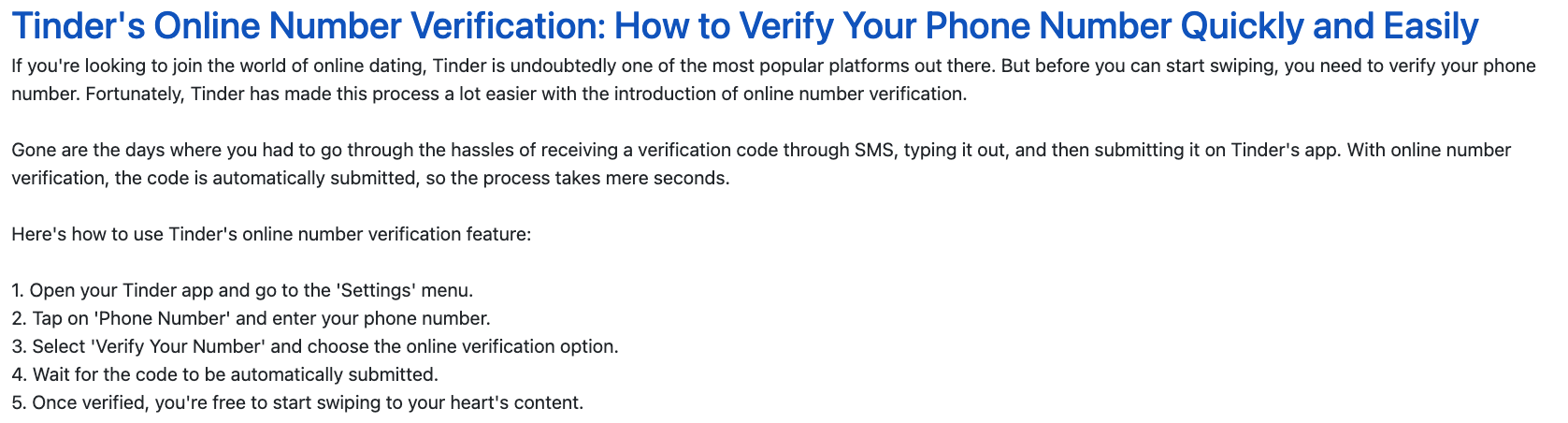
We observe the same types of messages for Tinder:
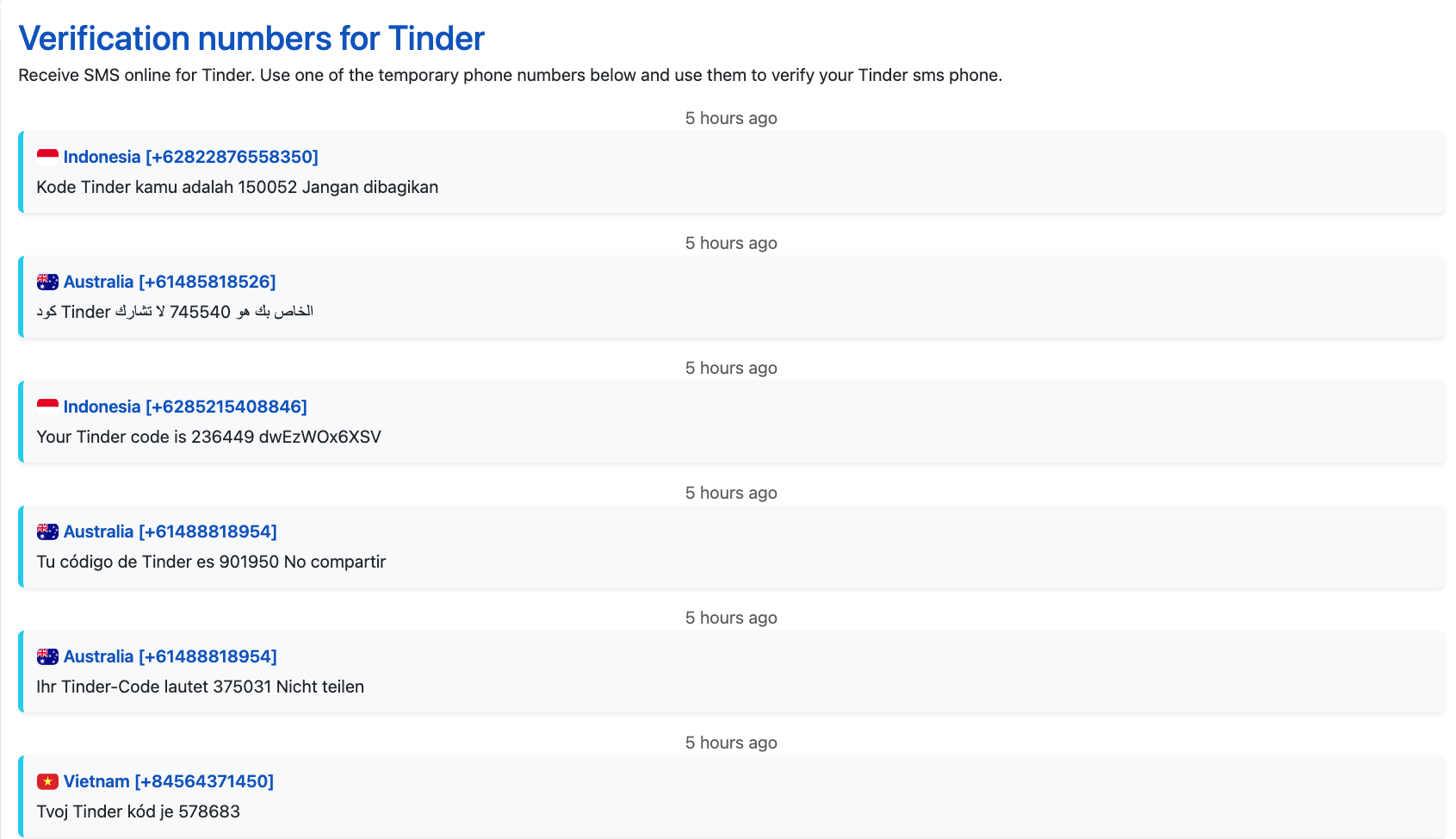
For Tinder, the website also optimises its SEO to target users trying to create Tinder accounts.
What are the consequences for applications targeted by temporary phone numbers, and what can they do about it?
- The main risk is related to fraud. Websites listing temporary phone numbers make it easy (and cheap) for fraudsters to create thousands of fake accounts. These accounts can then be used to conduct different types of fraud ranging from phishing, spam, spreading malware, or online dating scams.
- These fake accounts can also be used to bypass free plan limitations and avoid paying for the product. For example, in the case of ChatGPT, users can create dozens of accounts (multi-account) to avoid paying ChatGPT premium, all while being able to make a lot of queries.
- Attackers can also scale their fraud operation using bots to automate different actions such as creating fake accounts and sending spam messages.
- Sending SMS is not free. Thus, by sending verification codes to thousands of fake accounts you are spending money for users that won’t bring any value.
What can applications do against temporary phone numbers?
The first step is to detect if a user tries to register using a temporary phone number. I created a free API updated daily that you can use to obtain thousands of temporary phone numbers. Note that the same thing applies to email addresses, so I created another API to retrieve disposable email domains.
By blocking these temporary phone numbers and emails, you will make it more difficult and costly for attacks to create thousands of fake accounts, which will limit their capacity to use your application to spread malware, spam, or conduct any kind of fraud in general.
Why do services like sms24 provide free temporary phone numbers?
To better understand the incentives of these services I'd recommend deactivating your ad-blocker:
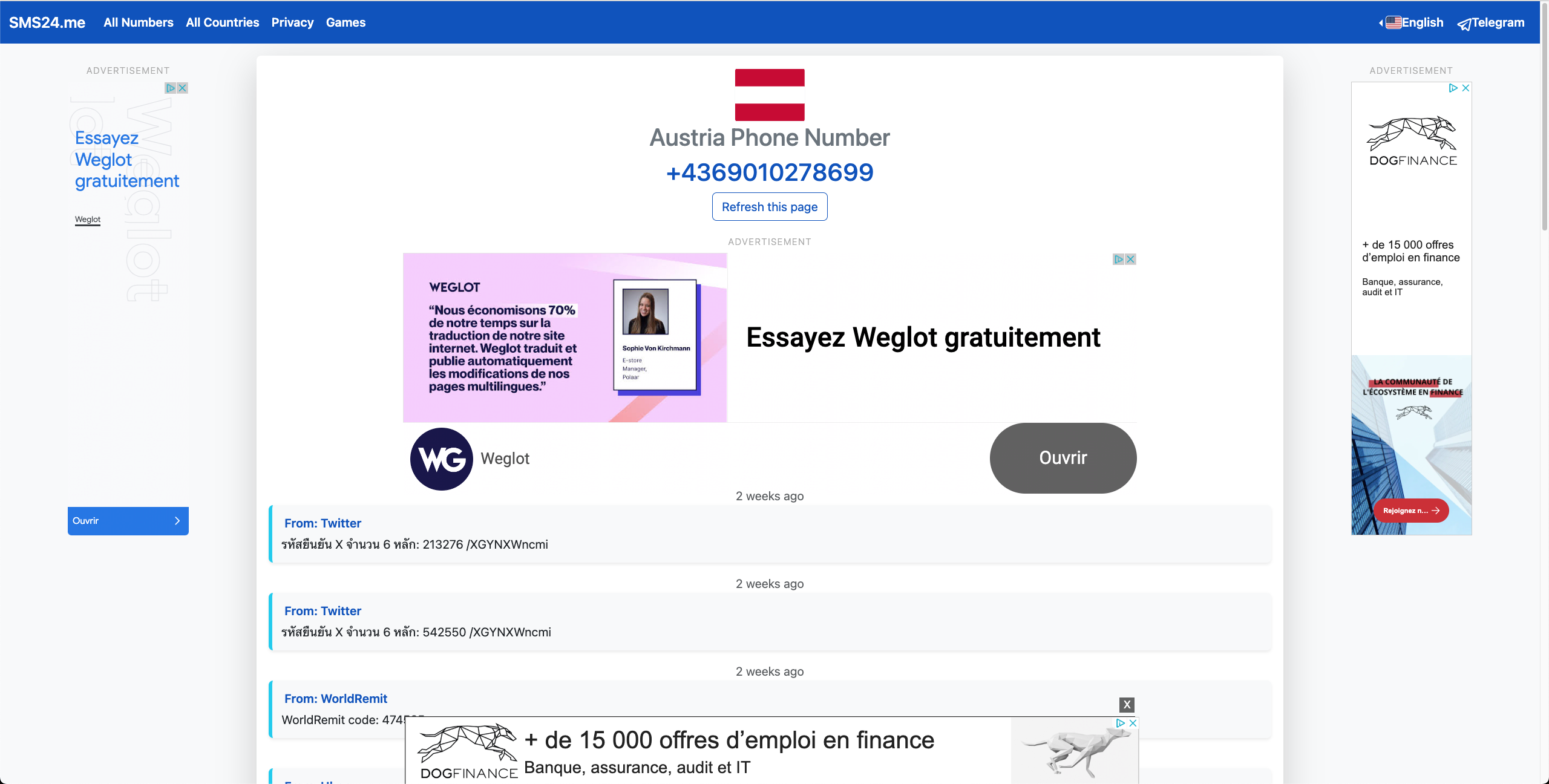
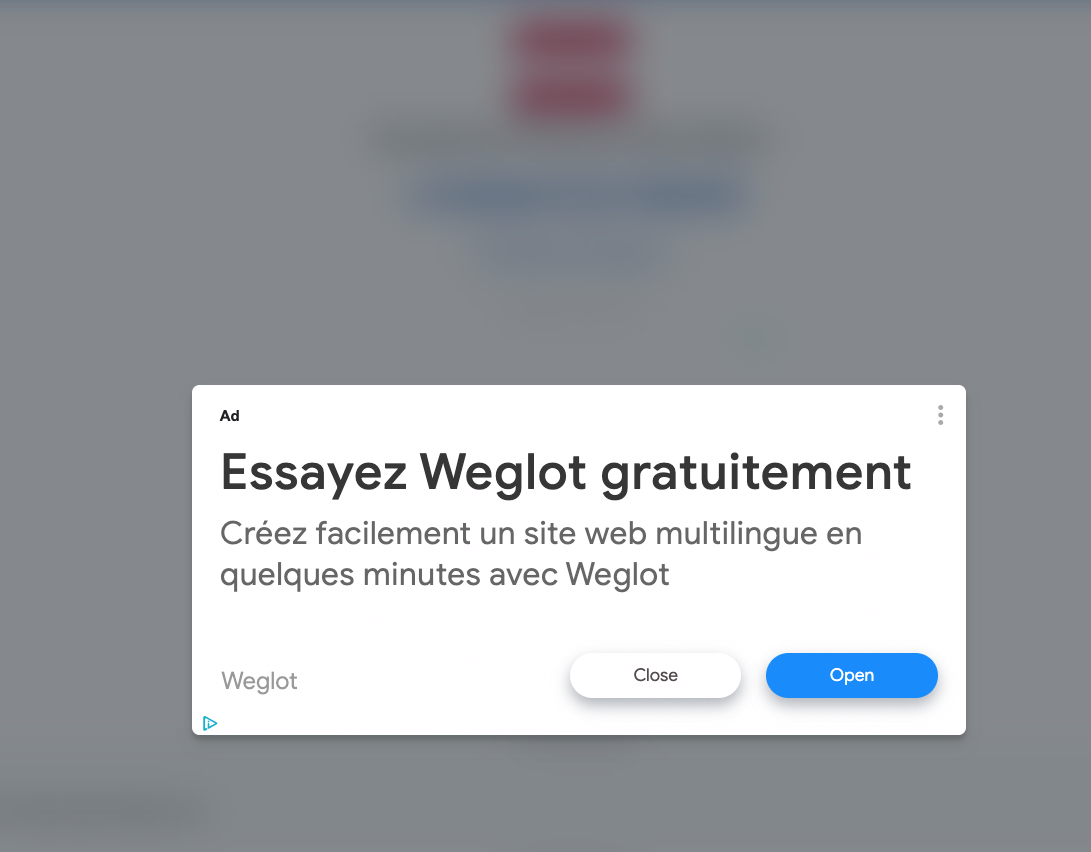
In the screenshot above, we see that the website is full of ads, which is certainly the main source of monetization of this website. Moreover, the website seems to randomly display ads that take the whole screen (cf screenshot below), which makes it more likely for a user to click on it by mistake. While this kind of practice is illegal and considered fraud (IVT traffic), it enables them to artificially increase their click rate and their ad revenue.
Conclusion
In this blog post, we analyzed 393,310 SMS related to 5,340 temporary phone numbers to better understand how temporary phone numbers are used, and which applications are targeted by them.
Our analysis showed that while all categories of applications are targeted, the most impacted are the following:
- Social networks: TikTok, Facebook and Instagram;
- Messaging/chat applications: Discord, Telegram and WhatsApp;
- Payment applications: Paypal;
- Search engine/email providers: Google, Microsoft and Apple;
- Transportation applications: Uber and Bolt.
By analyzing the content of the SMS received by these temporary phone numbers, we observed that most people leverage these numbers to create accounts without having to use a phone number tied to their identity.
These temporary phone number services represent a threat to websites and mobile applications as they are heavily used by fraudsters to create thousands of fake accounts to can be used to conduct scams, post spam, and spread malware.
The most simple way to protect your website against temporary phone numbers (and disposable emails) is to use an API that provides you with a list of temporary phone numbers and disposable emails so that you can prevent malicious users from creating accounts with these numbers.
Other recommended articles
Inside the IPIDEA residential proxy network disrupted by Google
This article provides an overview of the IPIDEA residential proxy network and how it was disrupted by Google.
Privacy leak: detecting anti-canvas fingerprinting browser extensions
In this article, we present 2 approaches that can be used to detect anti-canvas fingerprinting countermeasures and we discuss the potential consequences in terms of privacy for their users.
Fraud detection: how to detect if a user lied about its OS and infer its real OS?
In this article, we explain how we explain how you can detect that a user lied about the real nature of its OS by modifying its user agent. We provide different techniques that enable you to retrieve the real nature of the OS using JavaScript APIs such as WebGL and getHighEntropyValues.